https://www.garlic.com/~lynn/vnet1000.jpg
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Urban transportation Newsgroups: alt.folklore.computers Date: Sat, 20 Jun 2009 19:15:26 -0400Patrick Scheible <kkt@zipcon.net> writes:
reference in the above
http://www.boston.com/news/traffic/bigdig/articles/2008/07/17/big_digs_red_ink_engulfs_state/
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Is it possible to have an alternative payment system without riding on the Card Network platforms? Date: 21 June, 2009 Blog: Payment Systems Networklots of the stored value use the technology infrastructure ... POS terminals that connect to something .... but frequently the transactions are split off at some point before entering any association network.
Associations predate electronic transactions ... back when
associations were instrumental in getting brand acceptance at
merchants. With the advent of electronic transactions ... in large
part because of magstripe and pos-terminals ... a lot of this done at
los gatos lab (bldg. 29) .... wiki magstripe reference
https://en.wikipedia.org/wiki/Magnetic_stripe
and atm machines
https://en.wikipedia.org/wiki/IBM_3624
associations added value-added networks support (VANs ... common for lots of stuff in the period) for connectivity between merchant/acquirers and consumer/issuers.
in the past decade, there has been some legal challenges to the tight binding between association brands and the associations network interconnectivity.
Lobbying for the decade old bank modernization act ... claimed that a major point was precluding large non-bank institutions getting into traditional banking (at the top of the list was walmart and microsoft ... bank modernization act also repealed Glass-Steagall which plays a major role in the current financial mess).
More recently there was press that walmart was looking at buying an ILC ... so it could become its own acquirer (eliminating acquiring interchange fees) ... there was extensive lobbying against allowing permissions based on statements that walmart would also use the ILC for consumer issuing (at the time, they claimed that the ILC would only be used for acquiring).
There are some numbers that walmart accounts for 25-30 percent of retail payment transactions. Becoming their own acquirer would imply that they would eliminate that percentage of acquiring interchange fees. If they were to become an issuer ... then they would effectively eliminate the issuing interchange fees for those issued cards. And for the "on-us" transactions (i.e where they were both the issuer and the acquirer), it would also eliminate the association interchange fees.
In the mid-90s, some of the telcos were making forays into payment processing. There were a number of articles from the period that claimed telcos had a chance for taking over the payment processing business. It was partially predicated on anticipated huge volumes of micro-payments and only the telco callrecord processing platforms having the processing efficiency to handle the enormous explosion in transaction volumes. The transaction flow was also completely outside the traditional payment card processing platforms (and outside the high interchange fees).
Part of this is that many of the platforms were legacy from the early
days of being able to demonstrate that online/electronic processing
could satisfy the requirements for financial audits ... a recent
reference
https://www.garlic.com/~lynn/2008p.html#27 Father Of Financial Dataprocessing
It was largely the telco callrecord processing volumes that prompted more efficient implementations to handle the much higher transaction rates.
However, by the start of the current century ... nearly all that activity had evaporated. Part of it was explained by the micro-payment activity hadn't exploded as anticipated. The other explanation was that telcos were tolerant of fairly high default rates on statement/bills. As long as this represented charges for services ... it wasn't a enormous loss. However, after the telcos started getting into payment transactions and were doing merchant settlement ... consumer defaults (also) represented out-of-pocket money that had already been paid to merchants.
It was also in the mid-90s that saw the expansion of magstripe "stored-value" ... leveraging the POS terminal magstripe infrastructure ... but transactions were not being routed through the traditional payment networks and payment platforms.
From a technology standpoint ... ubiquitous cellphone and/or internet connectivity, starting in the mid-90s sounded the death knell for the value-added-networks (VANs). This is separate from the newer transaction technologies for handling the significant higher volumes for callrecords ... compared to the older transaction implementations found in the majority of financial processing implementations.
For a little topic drift ... recent discussion
https://www.garlic.com/~lynn/2009i.html#71 Barclays ATMs hit by computer fault
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: The computer did it Newsgroups: comp.arch Date: Sun, 21 Jun 2009 12:13:17 -0400Stephen Sprunk <stephen@sprunk.org> writes:
747 serial #3 was flying certification flights over seattle and I rented an apartment from one of the 747 engineers.
747 supposedly also had lot of design to be alternative to C5A for cargo plane operations ... including moving the pilot cockpit above the front of the plane ... so that the front could completely swing aside for onload/offload operations.
of course the other claim for the 747 was that because of increase in number of passengers ... there would be a minimum of two and usually four jetways used for passenger onload/offload.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: The computer did it Newsgroups: comp.arch Date: Sun, 21 Jun 2009 12:15:05 -0400Anne & Lynn Wheeler <lynn@garlic.com> writes:
... early version of cloud computing
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: IBM's Revenge on Sun Date: 21 June, 2009 Blog: Greater IBMIBM's Revenge on Sun and Microsoft's Brush with Reality
from above:
That means while it may go better than AT&Ts acquisition of NCR, or
IBM's acquisition of ROLM, it will have more similarities to the
problems associated to those out-of-competence zone acquisitions than
Oracle's typical work.
... snip ...
We were asked to come in and look at a number of things after that acquisition. One of the things we were told was that the people that were supposed to look at the books had no inkling that it was going into the red.
... clear any possible confusion regarding acquisition, referred to above, was the one in the 80s.
For other drift, some number of (former) IBM'ers were involved in startup doing 64bit sparc ... which was largely funded by foreign computer company and then outright absorbed. Reminded me of Amdahl at MIT seminar in the early 70s, talking about his new 370 clone processor startup ... and being grilled by some of the students in the audience about being a front for a foreign computer company.
Back in the day when we were doing ha/cmp product,
https://www.garlic.com/~lynn/subtopic.html#hacmp
we were involved with Ingres, Informix, Oracle and Sybase on cluster support. (At least) Both Informix and Oracle spent some amount of time explaining how they spent a lot of time modeling server processor support ... and lobbying heavily ... especially with SUN, for execution characteristics that were beneficial for DBMS workloads (significant part was processor cache size and operation).
Besides being on the transition to the loss side ... the reputation of the culture was more akin to that of Tandem's. I had already gotten blamed for online computer conferencing on the internal network in the late 70s and early 80s ... including there having been observations about visiting Jim there (after he had left SJR).
some old email reverences to Jim's departure to Tandem
https://www.garlic.com/~lynn/2007.html#email801006
https://www.garlic.com/~lynn/2007.html#email801016
Some of the computer conferencing stuff & visiting Jim at Tandem had
leaked outside the corporation and Datamation had done an article in
Nov81 ... some recently typed in part of that article
https://www.garlic.com/~lynn/2009i.html#29
That acquisition created another problem ... at least for me and my
HSDT effort
https://www.garlic.com/~lynn/subnetwork.html#hsdt
As part of HSDT, I was supposed to use at least some corporate hardware ... and only thing approaching "high-speed" was the aging 2701 T1 support (boxes that were 20+yrs old). FSD had done special bid "Zirpel" T1 cards for Series/1 (for customers that had some 2701s that were starting to fall apart). I was suppose to at least demonstrate IBM content ... even if it was as slow as T1.
One problem was that the acquisition was using aging DG processors ... and after the acquisition the business unit put in large order for something like 2-3yrs worth of S/1s ... and for a period, it was extremely difficult to obtain S/1s. I was actually able to get some of their S/1 order ... by trading them some other stuff for the S/1s.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Database Servers: Candy For Hackers Date: 22 June, 2009 Blog: Information SecurityDatabase Servers: Candy For Hackers
from above:
Good hackers today are businesspeople, assessing each target for the
simplest and most profitable attack scenarios. These days, there are
probably no plumper targets than enterprise databases
... snip ...
We had been called in to consult with small client/server startup that wanted to do payment transactions on their server and they had invented this technology called "SSL" they wanted to use; the result is now frequently referred to as electronic commerce.
Along the way, one of the must vulnerable points identified was the increasing use of RDBMS as part of merchant ecommerce servers ... which was identified as a major vulnerability. It wasn't so much that RDBMS were naturally more vulnerable ... but that the RDBMS component frequently would be the most complex part of a merchant electronic commerce environment ... and there is an old adage about vulnerability proportional to complexity.
For other topic drift ... old posts about the original relational/sql
implementation
https://www.garlic.com/~lynn/submain.html#systemr
An this oft reference post about meeting jan92 regarding RDBMS cluster
scale-up
https://www.garlic.com/~lynn/95.html#13
and two of the people mentioned at the above meeting later left and show up at the small client/server startup responsible for "commerce" server and wanted to implement payment transactions
cluster scale-up posts
https://www.garlic.com/~lynn/subtopic.html#hacmp
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: IBM's Revenge on Sun Date: 22 June, 2009 Blog: Greater IBMearlier post
One of the explanation for the contraction in the (non-mainframe) server market is the increasing/growing use of virtualization. For a couple decades dedicated servers per application were deployed ... in part, because hardware was cheaper than people skills to get multiple different applications to play nicely on the same server. A couple decades of this approach has resulted in huge farms of servers operating at 5-10% processor utilization. Virtualization has been providing 10:1 reduction/consolidation for some larger server farms ... with corresponding contraction in server market. This is something of a discontinuity as the (non-mainframe) server market adapts to virtualization consolidation.
By comparison, the mainframe market has tended to have the skill base to support mainframe operating near 100% utilization ... so it wouldn't be subject to a similar market virtualization consolidation.
Minor HA/CMP reference ... I had coined the name for our product to
reflect both the work on high availability ... as well as the work on
cluster scale-up .... old, periodically referenced meeting on cluster
scale-up (held in Larry's office):
https://www.garlic.com/~lynn/95.html#13
but as mentioned in the above, shortly after the meeting, the cluster scalup effort was transferred and we were told we couldn't work on anything with more than four processors ... however, I had been using ha/cmp so much ... the name remained.
Lots of old posts mentioning ha/cmp
https://www.garlic.com/~lynn/subtopic.html#hacmp
For the fun of it ... when we were doing ha/cmp, I was asked to write a section for the corporate continuous availability strategy document ... however, it was removed because both Rochester and POK said that they couldn't meet the implementation description (I had also coined the marketing terms disaster survivability and geographic survivability to differentiate from disaster/recovery) ... which may also have contributed to the scale-up work being transferred and getting told we couldn't work on anything with more than 4 processors.
related thread on (ibmconnect.com) greater ibm
https://www.garlic.com/~lynn/2009h.html#5 mainframe replacement
https://www.garlic.com/~lynn/2009h.html#8 Supercomputers and electronic commerce
misc. disaster survivability and geographic survivability posts:
https://www.garlic.com/~lynn/submain.html#available
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: 5in diskettes--any use? Newsgroups: alt.folklore.computers Date: Mon, 22 Jun 2009 15:06:17 -0400hancock4 writes:
some list of recovery:
https://www.garlic.com/~lynn/2006s.html#57 Turbo C 1.5 (1987)
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Fathers of Technology: 10 Unsung Heroes Newsgroups: alt.folklore.computers Date: Mon, 22 Jun 2009 16:59:55 -0400Fathers of Technology: 10 Unsung Heroes
and a couple from their list ...
Father of FORTRAN: John Backus
http://www.pcworld.com/article/167123-5/fathers_of_technology_10_unsung_heroes.html
Father of the mouse: Doug Engelbart
http://www.pcworld.com/article/167123-7/fathers_of_technology_10_unsung_heroes.html
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Intel, IBM spar for lead in Top 500 list Date: 23 June, 2009 Blog: High Performance ComputingIntel, IBM spar for lead in Top 500 list
from above:
Intel is on the rise in the world's fastest computers as ranked in the
latest Top 500 supercomputer list, but IBM Corp. is still top dog and
is making plans to keep it that way.
... snip ...
Germany, Saudi Arabia muscle into Top500 supercomputer list
http://www.networkworld.com/news/2009/062509-ibm-encryption.html
Top 500: Good Show for Nehalem, Germany, Arabia
http://www.internetnews.com/hardware/article.php/3826366/Top+500+Good+Show+for+Nehalem+Germany+Arabia.htm
Top 500 supers - world yawns at petaflops
http://www.theregister.co.uk/2009/06/23/top_500_supers_0609/
old background
https://www.garlic.com/~lynn/lhwemail.html#medusa
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: OT Kodachrome film discontinued Newsgroups: alt.folklore.computers Date: Wed, 24 Jun 2009 08:13:59 -0400Patrick Scheible <kkt@zipcon.net> writes:
although this says kodachrome 64 was introduced in 1974 ... so why
the processing lab didn't get it correct, I don't know.
https://en.wikipedia.org/wiki/Kodachrome
("K-14" process instead of "K-12"??)
I've got couple thousand or so slides in boxes someplace, mostly kodachrome ... maybe qtr have been digitized.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Is anyone aware of a system that offers three layers of security and ID protection for online purchases or even over the counter POS purchases? Date: 24 June, 2009 Blog: Payment Systems NetworkWe had been brought in to consult with small client/server startup that wanted to do payment transactions on their server ... they had also invented this technology called "SSL" they wanted to use; the result is now frequently called "electronic commerce".
Somewhat as a result, in the mid-90s, we were invited to participate in the X9A10 financial standard working group which had been given the requirement to preserve the integrity of the financial infrastructure for all retail payments (i.e. ALL as in debit, credit, stored-value, ACH, point-of-sale, unattended, low-value, high-value, transit turnstyle, internet, aka ALL).
Part of the effort was doing detailed end-to-end threat and
vulnerability studies of the various environments. At the top of the
list of threats and vulnerabilities was the ease that crooks could
harvest information from previous transactions (evesdropping,
skimming, data breaches) to use for fraudulent transactions. So part
of the x9.59 transaction standard was to slightly tweak the paradigm
to eliminate the usefulness of the information to the crooks ... some
references:
https://www.garlic.com/~lynn/x959.html#x959
X9.59 standard didn't do anything to prevent evesdropping, skimming, and/or data breaches ... it just slightly modified the paradigm to eliminate the usefulness of the information to the crooks. Now, the major use of SSL in the world, is this earlier activity we did for "electronic commerce", using SSL to hide financial transaction information. X9.59 standard eliminates this use of SSL, since it eliminates the requirement to hide the financial transaction information (as countermeasure to fraudulent transactions).
We've used a number of metaphors to characterize the current paradigm:
• security proportional to risk metaphor; in the current paradigm, the value of the information to the merchant is the profit on the transaction (possibly a couple dollars) and the value of the information to the processor can be a few cents per transaction ... while the value of the information to the crooks can be the credit limit and/or account balance (the crooks attacking the infrastructure may be able to outspend the merchant & processor defenders by a factor of one hundred times)
• dual-use vulnerability metaphor; in the current paradigm, the knowledge of the account number may be sufficient to perform a fraudulent transaction (effectively authentication, as such it needs to be kept confidential and never divulged anywhere) ... while at the same time the account number needs to be readily available for a large number of business processes. The conflicting requirements (never divulged and at the same time readily available) has led to comments that even if the planet was buried under miles of information hiding encryption, it still couldn't prevent information leakage.
A dual-use account paradigm analogy would be a userid/password scheme ... where there is no password and the userid must be made to do double duty ... used for lots & lots of processes (requiring it to be readily available) and at the same time used for authentication (requiring it to be kept confidential and never divulged).
An example would be requiring the userid to be publicly available for email purposes (i.e. email wouldn't be able to work w/o knowledge of the userid) ... but at the same time, knowledge of the userid would allow anybody to take over an account and impersonate the valid owner.
So all email headers (containing a userid) have to be kept encrypted and completely hidden so that it is never divulged ... but at the same time ... people needing to send you email have to know your userid (w/o knowing your userid)
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: IBM identity manager goes big on role control Date: 24 June, 2009 Blog: Greater IBMIBM identity manager goes big on role control
from above:
One major reason organisations have had to focus on roles in recent
years has been the need for compliance with legislation such as the US
Sarbanes-Oxley Act (SOX).
... snip ...
In the wake of Enron, Congress passed Sarbanes-Oxley ... placing much of the responsibility on SEC ... but didn't do anything about the underlying problem (which then resulted in AIG).
Possibly because GAO, didn't think that SEC was doing anything
... they started a database of financial filings with problems (which
supposedly should have been prosecuted by SEC ... at least under SOX)
https://www.gao.gov/products/gao-06-1079sp
from above:
The database consists of two files: (1) a file that lists 1,390
restatement announcements that we identified as having been made
because of financial reporting fraud and/or accounting errors between
July 1, 2002, and September 30, 2005, and (2) a file that lists 396
restatement announcements that we identified as having been made
because of financial reporting fraud and/or accounting errors between
October 1, 2005, and June 30, 2006.
... snip ...
Sarbanes-Oxley supposedly also had SEC doing something about the rating agencies (found to be "selling" triple-A ratings for toxic asset-backed securities) ... but there didn't appear to be anything except this report:
Report on the Role and Function of Credit Rating Agencies in the
Operation of the Securities Markets; As Required by Section 702(b) of
the Sarbanes-Oxley Act of 2002
http://www.sec.gov/news/studies/credratingreport0103.pdf
In the recent congressional hearings into Madoff Ponzi scheme, there was testimony by somebody that had been trying unsuccessfully for a decade to get SEC to do something about Madoff. Their repeated refrain was that while there was requirement for additional regulation, much more important was the need for visibility and transparency (fraud flourishes where there is lack of transparency) . They also mentioned that statistics show that "tips" expose 13 times more fraud than audits and that SEC has no "tips" hotline ... but SEC does have a hotline for corporations to complain about too vigorous investigations.
recent (archived) post with much longer discussion
https://www.garlic.com/~lynn/2009i.html#60 In the USA "financial regulator seeks power to curb excess speculation."
There have been jokes that SOX was a full employment for auditors and windfall for various vendors (w/o actually doing much)
In the past, I've periodically pontificated about RBAC as part of countermeasure to insider threats .... basically collections of permissions are formalized as roles ... as part of being able to define/require multi-person operations.
The attack against multi-person operations has been collusion. There was actually some amount of collusion countermeasures being worked on in the 80s (which somewhat got eclipsed with all the internet and worrying about external threats).
RBACs have also gotten into trouble when people didn't adequately align roles with actual business processes. Vulnerability was that the one person might be assigned multiple roles ... subverting objective of multi-person operation (as countermeasure to insider threats).
other recent posts mentioning SOX:
https://www.garlic.com/~lynn/2009.html#15 What are the challenges in risk analytics post financial crisis?
https://www.garlic.com/~lynn/2009.html#52 The Credit Crunch: Why it happened?
https://www.garlic.com/~lynn/2009.html#73 CROOKS and NANNIES: what would Boyd do?
https://www.garlic.com/~lynn/2009b.html#37 A great article was posted in another BI group: "To H*** with Business Intelligence: 40 Percent of Execs Trust Gut"
https://www.garlic.com/~lynn/2009b.html#54 In your opinion, which facts caused the global crise situation?
https://www.garlic.com/~lynn/2009b.html#57 Credit & Risk Management ... go Simple ?
https://www.garlic.com/~lynn/2009b.html#59 As bonuses...why breed greed, when others are in dire need?
https://www.garlic.com/~lynn/2009b.html#73 What can we learn from the meltdown?
https://www.garlic.com/~lynn/2009b.html#80 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#0 Audit II: Two more scary words: Sarbanes-Oxley
https://www.garlic.com/~lynn/2009c.html#1 Audit II: Two more scary words: Sarbanes-Oxley
https://www.garlic.com/~lynn/2009c.html#3 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#20 Decision Making or Instinctive Steering?
https://www.garlic.com/~lynn/2009c.html#29 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#44 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009d.html#0 PNC Financial to pay CEO $3 million stock bonus
https://www.garlic.com/~lynn/2009d.html#3 Congress Set to Approve Pay Cap of $500,000
https://www.garlic.com/~lynn/2009d.html#10 Who will Survive AIG or Derivative Counterparty Risk?
https://www.garlic.com/~lynn/2009d.html#22 Is it time to put banking executives on trial?
https://www.garlic.com/~lynn/2009d.html#37 NEW SEC (Enforcement) MANUAL, A welcome addition
https://www.garlic.com/~lynn/2009d.html#42 Bernard Madoff Is Jailed After Pleading Guilty -- are there more "Madoff's" out there?
https://www.garlic.com/~lynn/2009d.html#61 Quiz: Evaluate your level of Spreadsheet risk
https://www.garlic.com/~lynn/2009d.html#62 Is Wall Street World's Largest Ponzi Scheme where Madoff is Just a Poster Child?
https://www.garlic.com/~lynn/2009d.html#63 Do bonuses foster unethical conduct?
https://www.garlic.com/~lynn/2009d.html#73 Should Glass-Steagall be reinstated?
https://www.garlic.com/~lynn/2009d.html#75 Whistleblowing and reporting fraud
https://www.garlic.com/~lynn/2009e.html#0 What is swap in the financial market?
https://www.garlic.com/~lynn/2009e.html#13 Should we fear and hate derivatives?
https://www.garlic.com/~lynn/2009e.html#35 Architectural Diversity
https://www.garlic.com/~lynn/2009e.html#36 Architectural Diversity
https://www.garlic.com/~lynn/2009e.html#37 How do you see ethics playing a role in your organizations current or past?
https://www.garlic.com/~lynn/2009f.html#2 CEO pay sinks - Wall Street Journal/Hay Group survey results just released
https://www.garlic.com/~lynn/2009f.html#29 What is the real basis for business mess we are facing today?
https://www.garlic.com/~lynn/2009f.html#51 On whom or what would you place the blame for the sub-prime crisis?
https://www.garlic.com/~lynn/2009g.html#7 Just posted third article about toxic assets in a series on the current financial crisis
https://www.garlic.com/~lynn/2009g.html#33 Treating the Web As an Archive
https://www.garlic.com/~lynn/2009h.html#17 REGULATOR ROLE IN THE LIGHT OF RECENT FINANCIAL SCANDALS
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: PCI SSC Seeks Input on Security Standards Date: 24 June, 2009 Blog: Information Security NetworkPCI SSC Seeks Input on Security Standards
from above:
Merchants, processors, financial institutions and key stakeholders
have the opportunity to provide actionable feedback in an effort to
revise future editions of the Council's standards to improve payment
data security
... snip ...
also
PCI standards board asks PwC to review secure tech options
http://www.finextra.com/fullstory.asp?id=20183
from above:
The PCI Security Standards Council has asked PricewaterhouseCoopers
(PwC) to carry out research into technology that can be used by
merchants, service providers and processors to secure cardholder data.
... snip ...
We had been brought in to consult with small client/server startup that wanted to do payment transactions on their server ... they had also invented this technology called "SSL" they wanted to use; the result is now frequently called "electronic commerce".
Somewhat as a result, in the mid-90s, we were invited to participate in the X9A10 financial standard working group which had been given the requirement to preserve the integrity of the financial infrastructure for all retail payments (i.e. ALL as in debit, credit, stored-value, ACH, point-of-sale, unattended, low-value, high-value, transit turnstyle, internet, aka ALL).
Part of the effort was doing detailed end-to-end threat and
vulnerability studies of the various environments. At the top of the
list of threats and vulnerabilities was the ease that crooks could
harvest information from previous transactions (evesdropping,
skimming, data breaches) to use for fraudulent transactions. So part
of the x9.59 transaction standard was to slightly tweak the paradigm
to eliminate the usefulness of the information to the crooks ... some
references:
https://www.garlic.com/~lynn/x959.html#x959
X9.59 standard didn't do anything to prevent evesdropping, skimming, and/or data breaches ... it just slightly modified the paradigm to eliminate the usefulness of the information to the crooks. Now, the major use of SSL in the world, is this earlier activity we did for "electronic commerce", using SSL to hide financial transaction information. X9.59 standard eliminates this use of SSL, since it eliminates the requirement to hide the financial transaction information (as countermeasure to fraudulent transactions).
We've used a number of metaphors to characterize the current paradigm:
• security proportional to risk metaphor; in the current paradigm, the value of the information to the merchant is the profit on the transaction (possibly a couple dollars) and the value of the information to the processor can be a few cents per transaction ... while the value of the information to the crooks can be the credit limit and/or account balance (the crooks attacking the infrastructure may be able to outspend the merchant & processor defenders by a factor of one hundred times)
• dual-use vulnerability metaphor; in the current paradigm, the knowledge of the account number may be sufficient to perform a fraudulent transaction (effectively authentication, as such it needs to be kept confidential and never divulged anywhere) ... while at the same time the account number needs to be readily available for a large number of business processes. The conflicting requirements (never divulged and at the same time readily available) has led to comments that even if the planet was buried under miles of information hiding encryption, it still couldn't prevent information leakage.
A dual-use account paradigm analogy would be a userid/password scheme ... where there is no password and the userid must be made to do double duty ... used for lots & lots of processes (requiring it to be readily available) and at the same time used for authentication (requiring it to be kept confidential and never divulged).
An example would be requiring the userid to be publicly available for email purposes (i.e. email wouldn't be able to work w/o knowledge of the userid) ... but at the same time, knowledge of the userid would allow anybody to take over an account and impersonate the valid owner.
So everybody has to know your userid in order to send email ... but nobody can know your userid to prevent unauthorized access.
Note that PCI has been construed as response to the various data breach notification legislation.
We were tangentially involved in the (original) Cal. state data breach notification. We were brought in to help word smith the Cal. state electronic signature legislation and some of the organizations were also involved in privacy issues. They had done in-depth consumer surveys and the number one issue came out was "identity theft". A major component of that "identity theft" was fraudulent financial transactions against existing accounts (i.e. "account fraud") as the result of some sort of breach.
At the time, little or nothing seemed to being done about such data breaches (along with associated account fraud) and the organizations seem to feel that the publicity from breach notification might motivate countermeasures
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: OT Kodachrome film discontinued Newsgroups: alt.folklore.computers Date: Wed, 24 Jun 2009 14:09:19 -0400hancock4 writes:
it was several yrs ago ... i asked one of the offspring to do it. sent them 5-6 boxes (i think something like 600-700slides/box). they were suppose to get something good and I would pay for it. one of the issues was whether it was usb1 or usb2, the scanning and data transfer rate.
i got a cdrom of jpg files in return with 700+ images.
the jpg files don't contain any tag/info about device.
they are suppose to finish it someday if they get time ... or maybe one of their offspring (grandkids) can be induced to finish it.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: OT Kodachrome film discontinued Newsgroups: alt.folklore.computers Date: Wed, 24 Jun 2009 15:08:19 -0400Michael Black <et472@ncf.ca> writes:
ever watch the spy shows where the "break" into home ... take Polaroids of the rooms ... tear it apart looking for something ... and then use the Polaroids to put it all back like it was to begin with (so nobody can tell they had been there).
we've used phone cameras to take picture of things like kids clothing (we've found on sale) ... send the picture to (appropriate party) ... and in real time, ask if it is acceptable to purchase (for grandkids).
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: TIME's Annual Journey: 1989 Newsgroups: alt.folklore.computers Date: Wed, 24 Jun 2009 16:07:49 -0400TIME's Annual Journey: 1989
The Internet's Big Bang
http://www.time.com/time/specials/packages/article/0,28804,1902809_1902810_1905184,00.html
Look at how early HTML morphed from GML/SGML
http://infomesh.net/html/history/early/
SLAC visit to CERN and returning to deploy first webserver outside
europe/cern (on slac's virtual machine system):
http://www.slac.stanford.edu/history/earlyweb/history.shtml
science center was responsible for virtual machine systems
(initially cp40 and then cp67 which eventually morphed into
vm370)
https://www.garlic.com/~lynn/subtopic.html#545tech
and where GML was invented in 1969
https://www.garlic.com/~lynn/submain.html#sgml
and responsible for technology used in majority of the internal network
(larger than arpanet/internet from just about the beginning until
possibly late '85 or realy '86)
https://www.garlic.com/~lynn/subnetwork.html#internalnet
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Any one using JDBC type 4 to access IMS DB?? Newsgroups: bit.listserv.ibm-main Date: Wed, 24 Jun 2009 17:44:18 -0400Tom Longfellow <tlongfellow@verizon.net> writes:
Older Operating System Lingers, Holds Back ATM Services, Study Says
http://www.digitaltransactions.net/newsstory.cfm?newsid=2226
but then there is these items ...
Windows-based cash machines 'easily hacked'
http://news.cnet.com/Windows-based-cash-machines-easily-hacked/2100-7349_3-6233030.html
ATM malware lets criminals steal data and cash
http://news.cnet.com/8301-1009_3-10257277-83.html
Malware steals ATM accounts and PIN codes; Pwns ATMs under Windows XP
http://www.theinquirer.net/inquirer/news/1184568/malware-steals-atm-accounts-pin-codes
some recent ATM posts/discussions
https://www.garlic.com/~lynn/2009i.html#34 Data-sniffing trojans burrow into Eastern European ATMs
https://www.garlic.com/~lynn/2009i.html#71 Barclays ATMs hit by computer fault
and
https://www.garlic.com/~lynn/2009h.html#44 Book on Poughkeepsie
and recent post on addressing a "different" way of evesdropping/skimming
financial transaction vulnerabilities
https://www.garlic.com/~lynn/2009j.html#13 PCI SSC Seeks Input on Security Standards
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Another one bites the dust Newsgroups: bit.listserv.ibm-main,alt.folklore.computers Date: Wed, 24 Jun 2009 19:25:19 -0400BShannon@ROCKETSOFTWARE.COM (Bob Shannon) writes:
there was some resurgence in the early 80s with ACIS to try and get back into the education market; but it was lots of money being pumped in ... but didn't necessarily result in a of lot corporate business; lots of money went into supporting BITNET (& EARN in europe), big grants to MIT & Project Athena (x-windows, kerberos, other stuff), CMU (Andrew, Camelot, Mach ... vistiges of mach evolved into current system used by Apple), etc.
misc. posts mentioning bitnet & earn:
https://www.garlic.com/~lynn/subnetwork.html#bitnet
current ibm-main mailing list originated on bitnet.
other bitnet history
http://www.livinginternet.com/u/ui_bitnet.htm
from above:
The first BITNET connection was from CUNY to Yale University. By the end
of 1982 the network included 20 institutions. By the end of the 80's it
connected about 450 universities and research institutions and 3000
computers throughout North America and Europe. By the early 90's, BITNET
was the most widely used research communications network in the world
for email, mailing lists, file transfer, and real-time messaging.
... snip ...
history of bitnet listerv
http://www.lsoft.com/products/listserv-history.asp
from above:
In 1985, BITNET was THE academic network. The Internet did not exist
yet, and its ancestor, the ARPAnet, was still mostly a defense
network. A few US universities were connected to the ARPAnet, but in
Europe the only large, non dial-up network was BITNET. BITNET had a
Network Information Centre, called BITNIC or just "the NIC". Like most
BITNET sites at the time, the NIC was using an IBM mainframe running
VM/CMS.
... snip ...
BITNET used technology similar to the internal network, misc.
posts
https://www.garlic.com/~lynn/subnetwork.html#internalnet
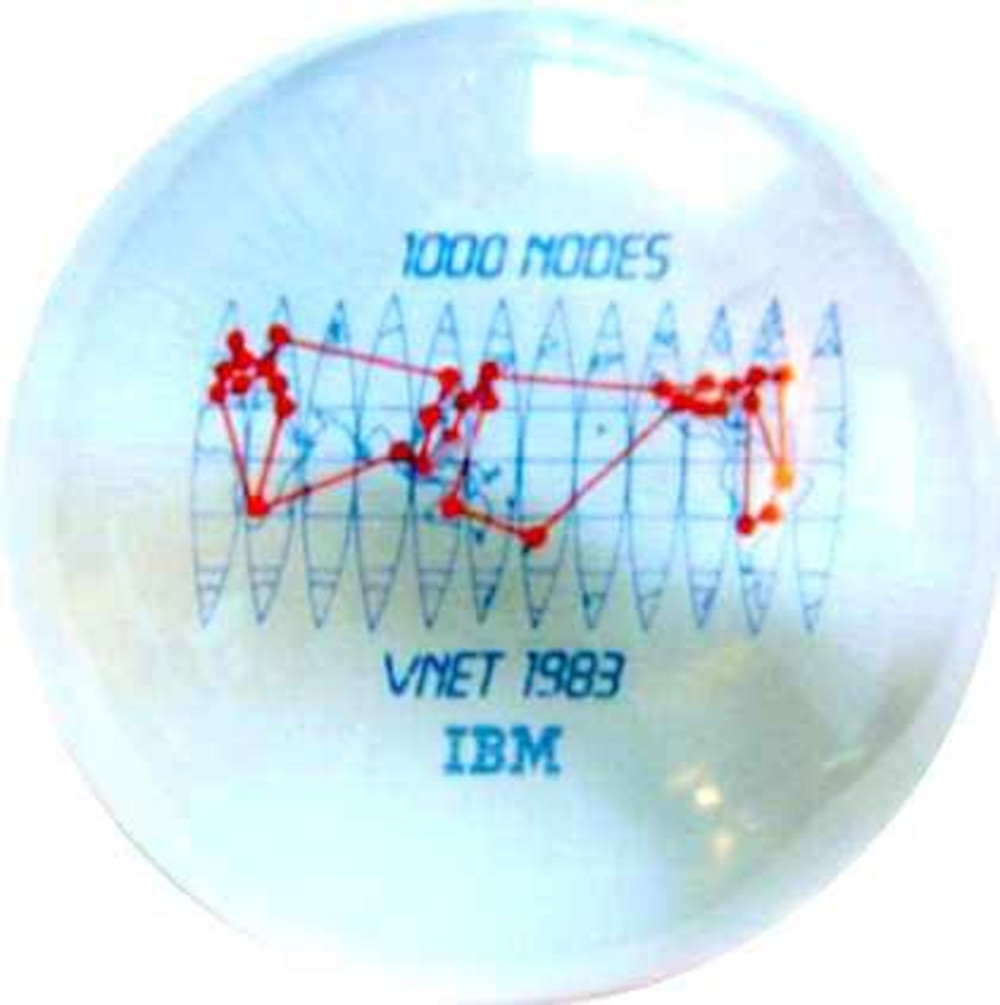
the internal network was larger than the arpanet/internet from just about the beginning until possibly late '85 or early '86 ... 1983 desk ornament for 1000th node on internal network

https://www.garlic.com/~lynn/vnet1000.jpg
and mostly technology that originated at the science center ... same
place that originated virtual machine technology (originally cp40, then
cp67 which eventually morphed into vm370)
https://www.garlic.com/~lynn/subtopic.html#545tech
misc old email related to internal network
https://www.garlic.com/~lynn/lhwemail.html#vnet
The arpanet conversion to internetworking protocol (TCP/IP) was 1/1/83
... which is the technology basis for modern internet. NSFNET backbone
is something of the operational basis for modern internet ... some
old email
https://www.garlic.com/~lynn/lhwemail.html#nsfnet
and CIX was the business basis for the modern internet.
article from today about the "WEB":
The Internet's Big Bang
http://www.time.com/time/specials/packages/article/0,28804,1902809_1902810_1905184,00.html
and a look at how early HTML morphed from GML/SGML
http://infomesh.net/html/history/early/
SLAC visit to CERN and returning to deploy first webserver outside
europe/cern (on slac's virtual machine system):
http://www.slac.stanford.edu/history/earlyweb/history.shtml
misc. past posts mentioning that GML was invented in
1969 at the science center:
https://www.garlic.com/~lynn/submain.html#sgml
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Another one bites the dust Newsgroups: bit.listserv.ibm-main,alt.folklore.computers Date: Wed, 24 Jun 2009 20:31:24 -0400Patrick Scheible <kkt@zipcon.net> writes:
one reason that it was cheaper is IBM may have "donated" a lot of the links (both in the US and in europe).
I use to have regular processes that looked for updates/changes at
ftp.nisc.sri.com (and retrieved it) before a lot of IETF stuff moved to
ftp.isi.edu ... where i get them now to maintain my standards index:
https://www.garlic.com/~lynn/rfcietff.htm
this is circa '85 reference to numbers of nodes; bitnet/earn smaller
than arpanet/internet ... which was smaller than the internal network;
BITNET 435
ARPAnet 1155
CSnet 104 (excluding ARPAnet overlap)
VNET 1650
EasyNet 4200
UUCP 6000
USENET 1150 (excluding UUCP nodes)
aka in '85 arpanet/internet nodes are about where internal network was
at in '83. arpanet/internet numbers was starting to accelerate in the
mid-80s (especially after the 1/1/83 change-over from IMPs to
internetworking protocol) ... while internal network increases started
to slow down as most of the internal mainframes from around the world
were brought on the network. The other big growth factor was that
workstations & PCs started to show up as internet/arpanet nodes ... and
internal network was maintaing policy that forced them to be treated as
emulated terminals.
misc. past posts mentioning above:
https://www.garlic.com/~lynn/2002k.html#26 DEC eNet: was Vnet : Unbelievable
https://www.garlic.com/~lynn/2006t.html#50 The Future of CPUs: What's After Multi-Core?
https://www.garlic.com/~lynn/2008l.html#2 IBM-MAIN longevity
https://www.garlic.com/~lynn/2008l.html#6 IBM-MAIN longevity
https://www.garlic.com/~lynn/2008l.html#7 IBM-MAIN longevity
https://www.garlic.com/~lynn/2008l.html#12 IBM-MAIN longevity
https://www.garlic.com/~lynn/2008m.html#18 IBM-MAIN longevity
https://www.garlic.com/~lynn/2008q.html#45 Usenet - Dead? Why?
https://www.garlic.com/~lynn/2008r.html#9 Comprehensive security?
EARN was bitnet in Europe ... reference to old email from somebody
looking for help getting EARN setup:
https://www.garlic.com/~lynn/2001h.html#email840320
in this post
https://www.garlic.com/~lynn/2001h.html#65 UUCP email
for a little topic drift ... the next/following post
https://www.garlic.com/~lynn/2001h.html#66 UUCP email
references in '93, getting a dish in the backyard for full usenet (satellite) feed at home (also co-authored article in jun '93 boardwatch ... bbs industry mag ... on drivers I wrote for the satellite modem).
some collected posts referencing some of the related early items
https://www.garlic.com/~lynn/internet.htm
last item in the above collection
https://www.garlic.com/~lynn/internet.htm#31
references a SJMN article from 24Sep99 about missing internet opportunity in 1980.
backyard dish for full (satellite) usenet feed (circa 1993)
https://www.garlic.com/~lynn/pagesat.jpg

--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Kaminsky interview: DNSSEC addresses cross-organizational trust and security Newsgroups: alt.folklore.computers Date: Thu, 25 Jun 2009 08:40:39 -0400re:
for a little internet topic drift ... the thing that translate URLs and
host names into IP addresses is the domain name system (DNS). The person
responsible for DNS had earlier done stint at the science center
https://www.garlic.com/~lynn/subtopic.html#545tech
Kaminsky interview: DNSSEC addresses cross-organizational trust and
security
http://searchsecurity.techtarget.com/news/interview/0,289202,sid14_gci1360143,00.html
from above:
DNS is the world's largest PKI without the 'K.'All DNSSEC does is it
adds keys. It takes this system that scales wonderfully and been a
success for 25 years,
... snip ...
Can you say AADS? ... various references
https://www.garlic.com/~lynn/x959.html#aads
Various posts regarding how DNSSEC represents catch-22 for
certification authority operation
https://www.garlic.com/~lynn/subpubkey.html#catch22
We had been called in to consult with this small client/server startup that wanted to do payment transactions on their server, they had also invented this technology called "SSL" they wanted to use ... the result is now frequently called "electronic commerce".
As part of the effort, we had to do some end-to-end walk thrus of
these new business operations calling themselves Certification
Authorities. Misc. past posts mentioning SSL domain name digital
certificates
https://www.garlic.com/~lynn/subpubkey.html#sslcerts
This shows up in DNSSEC where it is possible that the internet would
be able to obtain trusted real-time keys from the DNS infrastructure
w/o need for digital certificates. It also shows up in X9.59 financial
transaction standard protocol ... where the consumers' (issuing)
financial institution has prior relationship with the consumer.
Misc. x9.59 standard refrences
https://www.garlic.com/~lynn/x959.html#x959
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: The Big Takeover Date: 26 June, 2009 Blog: Greater IBMThe Big Takeover
from above:
The global economic crisis isn't about money - it's about power. How
Wall Street insiders are using the bailout to stage a revolution
... snip ...
The Dirty Dozen
http://www.rollingstone.com/politics/story/26868968/the_dirty_dozen
from above:
Meet the bankers and brokers responsible for the financial crisis -
and the officials who let them get away with it
... snip ...
One of the things from the period ... if individuals played at all, they would win big (the only way not to win was not to play) ... institutions might be caught holding toxic assets ... and have some downside ... but there effectively was no downside for individuals.
other pieces:
Taibbi's Goldman Sachs Takedown In Rolling Stone: Bank Has
'Unprecedented Reach And Power'
http://www.huffingtonpost.com/2009/06/25/taibbis-goldman-sachs-tak_n_220773.html
Rolling Stone: Goldman Sachs - The Wall Street Bubble Mafia
http://www.fundmymutualfund.com/2009/06/rolling-stone-goldman-sachs-wall-street.html
Goldman Sachs: "Engineering Ever Major Market Manipulation Since The
Great Depression"
http://zerohedge.blogspot.com/2009/06/goldman-sachs-engineering-every-major.html
Behind every bubble: Goldman Sachs
http://www.salon.com/tech/htww/2009/06/25/goldman_sachs/index.html
Rolling Stone: Goldman Sachs - The Wall Street Bubble Mafia
http://www.mrswing.com/articles/Rolling_Stone_Goldman_Sachs_The_Wall_Street_Bubble.html
related PBS program from a couple yrs ago:
the wall street fix
http://www.pbs.org/wgbh/pages/frontline/shows/wallstreet/
related time article
25 People to Blame for the Financial Crisis; Phil Gramm
http://content.time.com/time/specials/packages/article/0,28804,1877351_1877350_1877330,00.html
misc. past posts mentioning the PBS wall street fix program:
https://www.garlic.com/~lynn/2008f.html#13 independent appraisers
https://www.garlic.com/~lynn/2008f.html#46 independent appraisers
https://www.garlic.com/~lynn/2008f.html#71 Bush - place in history
https://www.garlic.com/~lynn/2008f.html#97 Bush - place in history
https://www.garlic.com/~lynn/2008g.html#2 Bush - place in history
https://www.garlic.com/~lynn/2008g.html#51 IBM CEO's remuneration last year ?
https://www.garlic.com/~lynn/2008g.html#66 independent appraisers
https://www.garlic.com/~lynn/2008h.html#89 Credit Crisis Timeline
https://www.garlic.com/~lynn/2008k.html#36 dollar coins
https://www.garlic.com/~lynn/2008k.html#41 dollar coins
https://www.garlic.com/~lynn/2008l.html#67 dollar coins
https://www.garlic.com/~lynn/2008l.html#70 dollar coins
https://www.garlic.com/~lynn/2008m.html#16 Fraud due to stupid failure to test for negative
https://www.garlic.com/~lynn/2008n.html#53 Your thoughts on the following comprehensive bailout plan please
https://www.garlic.com/~lynn/2008n.html#78 Isn't it the Federal Reserve role to oversee the banking system??
https://www.garlic.com/~lynn/2008n.html#82 Fraud in financial institution
https://www.garlic.com/~lynn/2008o.html#18 Once the dust settles, do you think Milton Friedman's economic theories will be laid to rest
https://www.garlic.com/~lynn/2008o.html#19 What's your view of current global financial / economical situation?
https://www.garlic.com/~lynn/2008o.html#28 Does anyone get the idea that those responsible for containing this finanical crisis are doing too much?
https://www.garlic.com/~lynn/2008o.html#37 The human plague
https://www.garlic.com/~lynn/2008o.html#51 Why are some banks failing, and others aren't?
https://www.garlic.com/~lynn/2008p.html#8 Global Melt Down
https://www.garlic.com/~lynn/2008p.html#9 Do you believe a global financial regulation is possible?
https://www.garlic.com/~lynn/2008q.html#26 Blinkenlights
https://www.garlic.com/~lynn/2008q.html#57 Blinkenlights
https://www.garlic.com/~lynn/2008q.html#61 Blinkenlights
https://www.garlic.com/~lynn/2008r.html#58 Blinkenlights
https://www.garlic.com/~lynn/2008r.html#64 Is This a Different Kind of Financial Crisis?
https://www.garlic.com/~lynn/2008s.html#9 Blind-sided, again. Why?
https://www.garlic.com/~lynn/2008s.html#20 Five great technological revolutions
https://www.garlic.com/~lynn/2008s.html#23 Garbage in, garbage out trampled by Moore's law
https://www.garlic.com/~lynn/2008s.html#35 Is American capitalism and greed to blame for our financial troubles in the US?
https://www.garlic.com/~lynn/2008s.html#55 Is this the story behind the crunchy credit stuff?
https://www.garlic.com/~lynn/2009.html#58 HONEY I LOVE YOU, but please cut the cards
https://www.garlic.com/~lynn/2009.html#84 what was the idea behind Citigroup's splitting up into two different divisions? what does this do for citigroup?
https://www.garlic.com/~lynn/2009b.html#36 A great article was posted in another BI group: "To H*** with Business Intelligence: 40 Percent of Execs Trust Gut"
https://www.garlic.com/~lynn/2009b.html#48 The blame game is on : A blow to the Audit/Accounting Industry or a lesson learned ???
https://www.garlic.com/~lynn/2009b.html#49 US disaster, debts and bad financial management
https://www.garlic.com/~lynn/2009b.html#52 What has the Global Financial Crisis taught the Nations, it's Governments and Decision Makers, and how should they apply that knowledge to manage risks differently in the future?
https://www.garlic.com/~lynn/2009b.html#53 Credit & Risk Management ... go Simple ?
https://www.garlic.com/~lynn/2009b.html#54 In your opinion, which facts caused the global crise situation?
https://www.garlic.com/~lynn/2009b.html#60 OCR scans of old documents
https://www.garlic.com/~lynn/2009b.html#73 What can we learn from the meltdown?
https://www.garlic.com/~lynn/2009b.html#80 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#0 Audit II: Two more scary words: Sarbanes-Oxley
https://www.garlic.com/~lynn/2009c.html#10 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#20 Decision Making or Instinctive Steering?
https://www.garlic.com/~lynn/2009c.html#29 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#36 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#38 People to Blame for the Financial Crisis
https://www.garlic.com/~lynn/2009c.html#42 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#44 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#55 Who will give Citigroup the KNOCKOUT blow?
https://www.garlic.com/~lynn/2009c.html#65 is it possible that ALL banks will be nationalized?
https://www.garlic.com/~lynn/2009d.html#10 Who will Survive AIG or Derivative Counterparty Risk?
https://www.garlic.com/~lynn/2009d.html#59 Quiz: Evaluate your level of Spreadsheet risk
https://www.garlic.com/~lynn/2009d.html#62 Is Wall Street World's Largest Ponzi Scheme where Madoff is Just a Poster Child?
https://www.garlic.com/~lynn/2009d.html#63 Do bonuses foster unethical conduct?
https://www.garlic.com/~lynn/2009d.html#73 Should Glass-Steagall be reinstated?
https://www.garlic.com/~lynn/2009d.html#77 Who first mentioned Credit Crunch?
https://www.garlic.com/~lynn/2009e.html#8 The background reasons of Credit Crunch
https://www.garlic.com/~lynn/2009e.html#23 Should FDIC or the Federal Reserve Bank have the authority to shut down and take over non-bank financial institutions like AIG?
https://www.garlic.com/~lynn/2009f.html#27 US banking Changes- TARP Proposl
https://www.garlic.com/~lynn/2009f.html#31 What is the real basis for business mess we are facing today?
https://www.garlic.com/~lynn/2009f.html#38 On whom or what would you place the blame for the sub-prime crisis?
https://www.garlic.com/~lynn/2009f.html#43 On whom or what would you place the blame for the sub-prime crisis?
https://www.garlic.com/~lynn/2009f.html#49 Is the current downturn cyclic or systemic?
https://www.garlic.com/~lynn/2009f.html#53 What every taxpayer should know about what caused the current Financial Crisis
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: A Complete History Of Mainframe Computing Newsgroups: alt.folklore.computers Date: Fri, 26 Jun 2009 14:54:47 -0400A Complete History Of Mainframe Computing
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Database Servers: Candy For Hackers Date: 27 June, 2009 Blog: Information Securityre:
Database Security: The First Three Steps
http://www.darkreading.com/database_security/security/app-security/showArticle.jhtml?articleID=218101607
from above:
Protecting sensitive data means locating and enumerating the
information in your databases -- and finding the right method to
secure it
... snip ...
IBM touts encryption innovation
http://www.networkworld.com/news/2009/070809-mastercard-halts-remote-pos-security.html
from above:
IBM today is saying one of its researchers has made it possible for
computer systems to perform calculations on encrypted data without
decrypting it.
... snip ...
Somewhat as a result of our earlier work on "electronic commerce", in
the mid-90s, we were invited to participate in the x9a10 financial
standard working group, which had been given the requirement to
preserve the integrity of the financial infrastructure for all retail
payments (i.e. this was *ALL*, as in debit, credit, stored-value, ACH,
point-of-sale, unattended, low-value, high-value, transit turnstyle,
internet, aka *ALL*). Part of this included detailed end-to-end threat
and vulnerability studies of the various environments. This resulted
in the x9.59 financial standard transaction protocol ... some
references
https://www.garlic.com/~lynn/x959.html#x959
Now one of the major threat and vulnerabilities is the ease which crooks can take information from transactions (skimming, evesdropping, data breaches) and use it for fraudulent transactions. Part of x9.59 was to slightly tweak the paradigm and eliminate the usefulness of this information to the crooks for fraudulent transactions (x9.59 didn't do anything to prevent data breaches, it just eliminated the financial fraud threat).
Now the major use of SSL in the world today is this earlier work we had done for electronic commerce as part of hiding transaction details ... but x9.59 eliminates the need to hide that information (as a countermeasure to preventing fraudulent transactions).
As an aside, somewhat as a result of the x9.59 and past database work ... I was asked to be one of two people writing the x9.99 financial privacy standard. This included having lots of meetings and revues regarding existing legislation like HIPAA, GLBA, EU-DPD ... as well as things like data breach notification legislation.
We had also been tangentially involved with the (first such legislation) Cal. state data breach notification legislation. We had been brought in to help word-smith the cal. state electronic signature act ... and several of the parties were also heavily involved in privacy issues. There had been detailed, in-depth consumer privacy studies and the number one issue was identity theft ... specifically was data breaches where the crooks were using the information for fraudulent financial transactions (major identity theft category). At the time there seemed to be little work in the area and the parties seemed to think that the publicity from breach notification might result in correction action and countermeasures.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Spy games play out at Russian consulate in San Francisco Date: 27 June, 2009 Blog: Information SecuritySpy games play out at Russian consulate in San Francisco
from above:
Pretend spies intent on swiping submarine plans were being hunted in
the Russian consulate in San Francisco as Friday morning neared.
... snip ...
There were different kind of spy games in the 80s.
The internal network ... misc. past posts
https://www.garlic.com/~lynn/subnetwork.html#internalnet
was larger than the arpanet/internet from just about the beginning until possibly late '85 or early '86. There was a requirement that all links leaving corporate premises had to be encrypted (there was a claim in '85 that the internal network had over half of all the link encryptors in the world). Part of the justification for all the encryption was not just corporate industrial espionage ... but also national industrial espionage.
In the 80s, there was a claim that the San Francisco Russian consulate had been chosen so that they had line-of-site to major west-coast microwave communication dish array (in san francisco) ... implication was for the purpose of evesdropping on all transmissions.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Database Servers: Candy For Hackers Date: 27 June, 2009 Blog: Information Securityre:
for this small client/server startup that had invented SSL and wanted to do payment transactions ... we had signoff authority on the implementation between the webserver and something called the payment gateway ... but could only make recommendations regarding implementation between webservers and browsers.
for the webserver to browser SSL use, there was an assumption that the user understood the relationship between the webserver they thot they were talking to and the URL they entered; the browser then used SSL to validate the correspondence between the URL and the webserver (the browser was connected to). The combination created the correspondence between the webserver that the user thot they were talking to and the webserver the browser was actually talking to.
almost immediately, webservers compromised SSL use. they had observed that SSL use cut their thruput by something like 90-95% ... and so they dropped back to using SSL with a checkout/pay button. The isse was that the user was no longer providing the URL that the browser was using SSL to check. Effectively, instead of SSL being used to complete correspondence validation between the webserver the user thot they were talking to and the webserver the browser was talking ... SSL was being used to validate the correspondence between what the webserver claimed to be (the URL supplied by the checkout/pay button) and the webserver the browser was talking to. this "click" paradigm ... also used in spam email ... undermined basic assumptions about integrity provided by SSL.
we did have a lot more control over the use of SSL in the webserver to
payment gateway ... some number of past posts discussing the payment
gateway (we periodically claim to be the original SOA)
https://www.garlic.com/~lynn/subnetwork.html#gateway
we mandated mutual SSL authentication ... which hadn't been in the original implementation (i.e. the webserver validating the payment gateway AND the payment gateway validating the webserver). The bigger problem we had with this part of the implementation was fault diagnostic and service level control. Traditional payment transaction trouble desk for leased line customers had objective of 5min first level problem determination. At the inception, this was before most ISPs had even heard of service level agreements. Early in trial deployments ... there was a trouble call, which after 3hrs, was closed as NTF (no trouble found).
We went back and looked at standard trouble desk resolution ... which was in large part based on circuit operations ... many of the features don't exist in packet environment. We created a fault diagnostic/recovery matrix ... half dozen or so states and a couple dozen kinds of outages or failures. For every point in the matrix, had to demonstrate either automatic recovery and/or capability for 5min first level problem/diagnostic determination. As part of being able to satisfy such a service level operation we had to invent some number of compensating procedures (to provide circuit-level capability in a packet environment).
Part of the SSL deployment for electronic commerce also involved doing
walk-thru & audits of these new business operations calling themselves
Certification Authorities ... which were issuing these things called
domain name SSL digital certificates ... misc. past posts discussing
SSL digital certificates
https://www.garlic.com/~lynn/subpubkey.html#sslcert
In the case of the webserver/gateway implementation ... it quickly became apparent that the digital certificates were redundant and superfluous. The webservers had to be registered at the payment gateway and the payment gateway had to be registered at the webservers ... and SSL digital certificates then became an anomalous side-effect of the SSL application library being used.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Price Tag for End-to-End Encryption: $4.8 Billion, Mercator Says Date: 27 June, 2009 Blog: Information SecurityPrice Tag for End-to-End Encryption: $4.8 Billion, Mercator Says
from above:
Meanwhile, the final tab for the solution is no small matter. A
point-of-sale terminal with end-to-end encryption starts at $500 for a
mom-and-pop merchant and goes up for multi-lane retailers, the report
notes.
... snip ...
As we've pontificated several times before ... that in the current paradigm, even if the planet were buried under miles of information hiding encryption, it still wouldn't prevent information linkage.
misc. comments about past news articles on the subject:
https://www.garlic.com/~lynn/2009f.html#36 PCI security rules may require reinforcements
https://www.garlic.com/~lynn/2009f.html#57 Data masking/data disguise Primer 1) WHY
https://www.garlic.com/~lynn/2009g.html#10 Top 10 Cybersecurity Threats for 2009, will they cause creation of highly-secure Corporate-wide Intranets?
https://www.garlic.com/~lynn/2009g.html#11 Top 10 Cybersecurity Threats for 2009, will they cause creation of highly-secure Corporate-wide Intranets?
https://www.garlic.com/~lynn/2009g.html#46 What's your personal confidence level concerning financial market recovery?
https://www.garlic.com/~lynn/2009g.html#52 Future of Financial Mathematics?
https://www.garlic.com/~lynn/2009h.html#3 Consumer Credit Crunch and Banking Writeoffs
https://www.garlic.com/~lynn/2009h.html#29 Analysing risk, especially credit risk in Banks, which was a major reason for the current crisis
https://www.garlic.com/~lynn/2009i.html#20 Online Banking's Innate Security Flaws
https://www.garlic.com/~lynn/2009i.html#53 Merchant Groups Ask for Broad Changes in Letter to PCI's Overseer
https://www.garlic.com/~lynn/2009i.html#64 Weak security enables credit card hacks
https://www.garlic.com/~lynn/2009i.html#68 Weak security enables credit card hacks
https://www.garlic.com/~lynn/2009j.html#13 PCI SSC Seeks Input on Security Standards
https://www.garlic.com/~lynn/2009j.html#25 Database Servers: Candy For Hackers
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Usability and security gurus agree that masked passwords should go Date: 30 June, 2009 Blog: Computer Security and ForensicsMasked passwords must go
from above:
Nielsen said that sites usually blank out type-in passwords out of
force of habit rather than reason. "Password masking has become common
for no reasons other than (a) it's easy to do, and (b) it was the
default in the web's early days," he said
... snip ...
Actually it dates back to when online terminals were more like typewriters ... that involved rolls of physical paper ... and entering password would result in the typed characters surviving on real paper. From the 60s, there was process that passwords were eight characters or less ... and would first type series of eight characters ... backspace, repeat with other characters, backspace and repeat again. There was study of what combination of three overprinted characters would best mask any combination of typed password characters.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Malware steals ATM accounts and PIN codes; Pwns ATMS user Windows XP Date: 30 June, 2009 Blog: Computer Security and Forensicsre:
Back in the late 80s when we start ha/cmp effort ... some past posts
https://www.garlic.com/~lynn/subtopic.html#hacmp
we did some number of threat & vulnerability studies (not solely
security ... also general assurance and availability). We identified
some number of vulnerabilities in tcp/ip protocol and
implementations. We also identified C language usage as particularly
vulnerable to buffer overflow problems. Lots of related past posts
https://www.garlic.com/~lynn/subintegrity.html#overflow
We had been involved in a pascal language tcp/ip implementation
... which never had any of the common vulnerabilities found in C
language implementations. Some posts about "tweaking" the pascal
language implementation and getting nearly three orders of magnitude
thruput improvement (in terms of bytes moved per instruction executed,
based on some testing done at Cray Research)
https://www.garlic.com/~lynn/subnetwork.html#1044
There have also been some number of studies of major implementations done in various other languages ... also which have had none of the common vulnerabilities common to C language implementations
A slightly related recent post mentioning old-time ATM implementations
(mostly from the 70s)
https://www.garlic.com/~lynn/2009j.html#17
somewhat related:
Researcher barred for demoing ATM security vuln
http://www.theregister.co.uk/2009/06/30/atm_talk_canceled/
from above:
A talk demonstrating security weaknesses in a widely used automatic
teller machine has been pulled from next month's Black Hat conference
after the machine vendor placed pressure on the speaker's employer.
... snip ...
Juniper Nixes ATM Security Talk
http://www.pcworld.com/businesscenter/article/167648/juniper_nixes_atm_security_talk.html
ATM Vendor Halts Researcher's Talk on Vulnerability
http://www.wired.com/threatlevel/2009/06/atm-vendor-halts-talk/
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Price Tag for End-to-End Encryption: $4.8 Billion, Mercator Says Date: 30 June, 2009 Blog: Payment Systems Networkre:
recent news item (somewhat related footnote):
Report: Data-Stealing Malware Leads To Rise In Cybercrime, Cyberterrorism
http://www.darkreading.com/insiderthreat/security/cybercrime/showArticle.jhtml?articleID=218101832
from above:
In its first Focus Report, Trend Micro examines the growth of
data-stealing malware, its characteristics, and its roots in the
underground cyber crime economy
... snip ...
In some cases, calculations are about provisioning costs ... which isn't just the price of the device ... but the fully loaded burden of replacing the old device with the new device.
One of the studies early in this decade ... as part of a large pilot with a "chip" payment card ... the total provisioning costs for replacing POS device was relatively insensitive to the features in the device. of course that pilot was in the YES CARD period ... and subsequently all trace of the pilot appears to have evaporated
old reference to cartes 2002 presentation about it being trivial to
create counterfeit chipcard
https://web.archive.org/web/20030417083810/http://www.smartcard.co.uk/resources/articles/cartes2002.html
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: An Amazing Document On Madoff Said To Have Been Sent To SEC In 2005 Date: 1 July, 2009 Blog: Greater IBMAn Amazing Document On Madoff Said To Have Been Sent To SEC In 2005
In the congressional hearings into Madoff ponzi scheme, he testified that he had tried unsuccessfully for a decade to get SEC to do something about Madoff. There was even an interview the day after the hearings with his lawyer. The laywer said that he didn't want to appear in public unnecessarily since about the only explanation that he had come up for SEC inaction was heavy (violent) criminal connections (which conceivably would place his life in danger).
One of the themes thru the testimony was that while new regulations are required, much more important is transparency and visibility. Also, "tips" turn up 13 times more fraud than audits. SEC doesn't have a "tip" hotline ... but has a hotline for companies to complain about investigations.
The "tip" scenario somewhat relates to passing of Sarbanes-Oxley. There are a number of articles that have referred to Gramm's favor for Enron
Gramm and the 'Enron Loophole'
http://www.nytimes.com/2008/11/17/business/17grammside.html
Phil Gramm's Enron Favor
https://web.archive.org/web/20080711114839/http://www.villagevoice.com/2002-01-15/news/phil-gramm-s-enron-favor/
25 People to Blame for the Financial Crisis; Phil Gramm
http://content.time.com/time/specials/packages/article/0,28804,1877351_1877350_1877330,00.html
In the wake of ENRON, Congress passed Sarbanes-Oxley (sometimes jokes about full employment for auditors) ... but didn't do anything about the underlying problem, which led to AIG.
Possibly because GAO, also didn't think that SEC was doing much
... they started a database of financial filings with problems (which
supposedly should have been prosecuted by SEC ... at least under SOX)
https://www.gao.gov/products/gao-06-1079sp
from above:
The database consists of two files: (1) a file that lists 1,390
restatement announcements that we identified as having been made
because of financial reporting fraud and/or accounting errors between
July 1, 2002, and September 30, 2005, and (2) a file that lists 396
restatement announcements that we identified as having been made
because of financial reporting fraud and/or accounting errors between
October 1, 2005, and June 30, 2006.
... snip ...
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: password safes for mac Date: Wed, 01 Jul 2009 17:47:37 -0400 MailingList: cryptograpyOn 07/01/2009 02:10 PM, Nicolas Williams wrote:
In the late 90s, there was work on EU FINREAD standard for external
trusted card-acceptor device ... that had trusted pin-entry and
trusted display. The objective was countermeasure to lots of well
known compromises of PCs (including keylogger ... implying that
compromised PC could operate an external hardware token, even if PIN
was required per transaction). misc. past posts mentioning FINREAD
https://www.garlic.com/~lynn/subintegrity.html#findread
A lot of this evaporated in the early part of this decade in the wake of various troubles associated with hardware tokens.
As an aside ... one of the things we did in the AADS patent portfolio was to remove business rules from the hardware token ... as part of enabling person-centric operation (i.e. the same token might be used for lots of different environments ... as opposed to having hardware token for every unique business environment).
An AADS hardware token can support both single-factor as well as multi-factor authentication operation ... but it is up to the business application interacting with the hardware token to indicate the amount of authentication & integrity (some assumption about security proportional to risk ... for instance, whether or not PIN might be required for every operation, or at all).
AADS patent portfolio summary
https://www.garlic.com/~lynn/aadssummary.htm
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Do Social Media Sites Spawn Socially Unacceptable and Politically Incorrect Outbursts? Date: 1 July, 2009 Blog: Old Geek RegistryI got blamed for computer conferencing on the internal network in the late 70s and early 80s ... the internal network was larger than the arpanet/internet from just about the beginning until possibly late 85 or early 86 ... some past posts/references
Somewhat as a result, there was a researcher that was paid to sit in the back of my office for nine months ... taking notes on how I communicated. They also got copies of all my incoming and outgoing email and logs of all instant messages. The results was a corporate research report, a stanford phd thesis (joint between language and computer ai) and some number of other papers and books.
Part of the analysis was that computer mediated communication lacks the visual and auditory real-time (social) queues that help mediate acceptable social behavior.
The internet environment can further aggravate the situation if there is a degree of anonymity ... creating a sense of no repercussions or consequences.
There was a recent, semi-related article looking at genetic basis for extreme risk taking behavior (in the recent financial meltdown), extreme focus on immediate rewards and limited/impaired sense of future consequences
misc. past posts mentioning computer mediated communication
https://www.garlic.com/~lynn/subnetwork.html#cmc
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: IBM touts encryption innovation Date: 2 July, 2009 Blog: Greater IBMIBM touts encryption innovation
from above:
IBM today is saying one of its researchers has made it possible for
computer systems to perform calculations on encrypted data without
decrypting it.
... snip ...
mentioned:
https://www.garlic.com/~lynn/2009j.html#22 A Complete History Of Mainframe Computing
we did something different for financial transaction information ... which has been involved in most of the breaches that have been in the news.
We had been brought in to consult with small client/server startup that wanted to do payment transactions on their server ... they had also invented this technology called "SSL" they wanted to use; the result is now frequently called "electronic commerce".
Somewhat as a result, in the mid-90s, we were invited to participate in the X9A10 financial standard working group which had been given the requirement to preserve the integrity of the financial infrastructure for all retail payments (i.e. *ALL* as in debit, credit, stored-value, ACH, point-of-sale, unattended, low-value, high-value, transit turnstyle, internet, aka *ALL*).
Part of the effort was doing detailed end-to-end threat and
vulnerability studies of the various environments. At the top of the
list of threats and vulnerabilities was the ease that crooks could
harvest information from previous transactions (evesdropping,
skimming, data breaches) to use for fraudulent transactions. So part
of the x9.59 transaction standard was to slightly tweak the paradigm
to eliminate the usefulness of the information to the crooks ... some
references:
https://www.garlic.com/~lynn/x959.html#x959
X9.59 standard didn't do anything to prevent evesdropping, skimming, and/or data breaches ... it just slightly modified the paradigm to eliminate the usefulness of the information to the crooks. Now, the major use of SSL in the world, is this earlier activity we did for "electronic commerce", using SSL to hide financial transaction information. X9.59 standard eliminates this use of SSL, since it eliminates the requirement to hide the financial transaction information (as countermeasure to fraudulent transactions).
We've used a number of metaphors to characterize the current paradigm:
• security proportional to risk; in the current paradigm, the value of the information to the merchant is the profit on the transaction (possibly a couple dollars) and the value of the information to the processor can be a few cents per transaction ... while the value of the information to the crooks can be the credit limit and/or account balance (the crooks attacking the infrastructure may be able to outspend the merchant & processor defenders by a factor of one hundred times)
• dual-use vulnerability; in the current paradigm, the knowledge of the account number may be sufficient to perform a fraudulent transaction (effectively authentication, as such it needs to be kept confidential and never divulged anywhere) ... while at the same time the account number needs to be readily available for a large number of business processes. The conflicting requirements (never divulged and at the same time readily available) has led to comments that even if the planet was buried under miles of information hiding encryption, it still couldn't prevent information leakage.
A dual-use account paradigm analogy would be a userid/password scheme ... where there is no password and the userid must be made to do double duty ... used for lots & lots of processes (requiring it to be readily available) and at the same time used for authentication (requiring it to be kept confidential and never divulged).
An example would be requiring the userid to be publicly available for email purposes (i.e. email wouldn't be able to work w/o knowledge of the userid) ... but at the same time, knowledge of the userid would allow anybody to take over an account and impersonate the valid owner.
So all email headers (containing a userid) have to be kept encrypted and completely hidden so that it is never divulged ... but at the same time ... people needing to send you email have to know your userid (w/o knowing your userid)
Periodically in the past, we've commented that even if the planet was buried under miles of information hiding encrypting, it still wouldn't stop information leakage.
Database Servers: Candy For Hackers
http://www.informationweek.com/news/security/attacks/showArticle.jhtml?articleID=218100141&cid=RSSfeed_IWK_Security
from above:
Good hackers today are businesspeople, assessing each target for the
simplest and most profitable attack scenarios. These days, there are
probably no plumper targets than enterprise databases
... snip ...
Database Security: The First Three Steps
http://www.darkreading.com/database_security/security/app-security/showArticle.jhtml?articleID=218101607
from above:
Protecting sensitive data means locating and enumerating the
information in your databases -- and finding the right method to
secure it
... snip ...
As an aside, somewhat as a result of the x9.59 and past database work ... I was asked to be one of two people writing the x9.99 financial privacy standard draft. This included having lots of meetings and revues regarding existing legislation like HIPAA, GLBA, EU-DPD ... as well as things like data breach notification legislation.
We had also been tangentially involved with the (first such legislation) Cal. state data breach notification legislation. We had been brought in to help word-smith the cal. state electronic signature act ... and several of the parties were also heavily involved in privacy issues. There had been detailed, in-depth consumer privacy studies and the number one issue was identity theft ... specifically was data breaches where the crooks were using the information for fraudulent financial transactions (major identity theft category). At the time there seemed to be little work in the area and the parties seemed to think that the publicity from breach notification might result in correction action and countermeasures.
related subject:
Price Tag for End-to-End Encryption: $4.8 Billion, Mercator Says
http://www.digitaltransactions.net/newsstory.cfm?newsid=2250
from above:
Meanwhile, the final tab for the solution is no small matter. A
point-of-sale terminal with end-to-end encryption starts at $500 for a
mom-and-pop merchant and goes up for multi-lane retailers, the report
notes.
... snip ...
As we've pontificated several times before ... that in the current paradigm, even if the planet were buried under miles of information hiding encryption, it still wouldn't prevent information linkage.
misc. comments about past news articles on the subject:
https://www.garlic.com/~lynn/2009f.html#36 PCI security rules may require reinforcements
https://www.garlic.com/~lynn/2009f.html#57 Data masking/data disguise Primer 1) WHY
https://www.garlic.com/~lynn/2009g.html#10 Top 10 Cybersecurity Threats for 2009, will they cause creation of highly-secure Corporate-wide Intranets?
https://www.garlic.com/~lynn/2009g.html#11 Top 10 Cybersecurity Threats for 2009, will they cause creation of highly-secure Corporate-wide Intranets?
https://www.garlic.com/~lynn/2009g.html#46 What's your personal confidence level concerning financial market recovery?
https://www.garlic.com/~lynn/2009g.html#52 Future of Financial Mathematics?
https://www.garlic.com/~lynn/2009h.html#3 Consumer Credit Crunch and Banking Writeoffs
https://www.garlic.com/~lynn/2009h.html#29 Analysing risk, especially credit risk in Banks, which was a major reason for the current crisis
https://www.garlic.com/~lynn/2009i.html#20 Online Banking's Innate Security Flaws
https://www.garlic.com/~lynn/2009i.html#53 Merchant Groups Ask for Broad Changes in Letter to PCI's Overseer
https://www.garlic.com/~lynn/2009i.html#64 Weak security enables credit card hacks
https://www.garlic.com/~lynn/2009i.html#68 Weak security enables credit card hacks
https://www.garlic.com/~lynn/2009j.html#13 PCI SSC Seeks Input on Security Standards
https://www.garlic.com/~lynn/2009j.html#25 Database Servers: Candy For Hackers
... followup
maybe (ansi) x9.15? it was effort to try and standardize POS-terminal to merchant acquiring protocol. At the time, it didn't really catch on, most of the merchant acquirers already had several protocol specifications and there wasn't enuf motivation to converge.
For instance, when we were brought in to consult with small
client/server startup because they wanted to do payment transactions
on their server (previously mentioned) ... a message
protocol/specification was used that was prevalent in the hotel and
las vegas casino industry. The messages were sent over the internet
between webservers and payment gateway, tunneled thru SSL
... misc. past posts mentioning payment gateway
https://www.garlic.com/~lynn/subnetwork.html#gateway
There were later other activities to do specifications for internet
payment protocol ... but just taking existing message formats and
putting them on the internet wouldn't provide the same level of
service. For instance, it was common in the deployments for large
hotels & casinos to have leased-lines to the merchant
acquirer. The trouble desk at the merchant acquirer had
(circuit-oriented) diagnostic processes ... like loop-back to the
local & remote modems, loop-back at the low-level driver interfaces,
loop-back at the application level. As referenced in this recent post,
simple translation of the messages from circuit-based environment to
packet-based environment wouldn't provide equivalent service levels:
https://www.garlic.com/~lynn/2009j.html#25 Database Servers: Candy For Hackers
... and so we had to invent compensating (diagnostic) processes in attempt to raise service level operation (one criteria was 5mins elapsed for 1st level problem determination).
One of the side-effects of the X9A10 financial standard working group
having been given the requirement to preserve the integrity of the
financial infrastructure for all retail payments ... was we had to
look at end-to-end operation for *ALL* retail payments. Some of the
other internet-specific payment specification efforts from the period
weren't similarly constrained (and/or even needed to really know how
legacy payment transactions happened). For instance, several of the
specifications had enormous payment transaction payload and processing
*bloat* (by factor of two orders of magnitude, one hundred times
increase). Faced with never being able to integrate into the actual
payment processing infrastructure they had to define complex gateways
that stripped off the enormous bloat and reformated for traditional
payment infrastructure (as opposed to tweaking message formats
slightly and enormously simplified gateway that moved effectively the
same message from internet and payment infrastructure). Misc. past
posts mentioning enormous bloat of some of the other payment
specifications
https://www.garlic.com/~lynn/subpubkey.html#bloat
Now in relatively recent 5-year review of (ISO) 8583 (international payment networking standard) ... a POS-terminal to merchant acquiring standard was added to the standard and x9.15 was withdrawn.
As to some (ISO) x.5xx standard stuff ... there was an acm sigmod annual meeting in san jose in the early 90s, and during one of the sessions, somebody in the audience asked what was all this (ISO) x.5xx about ... and the reply was that it was some networking engineers attempting to reinvent 1960s database technology.
As to (ISO) X.25 ... in the late 80s, my wife served brief stint as chief architect for Amadeus (european airline res system ... sort of started from the eastern airlines res system). She had backed the decision to go with x.25 ... which brought down the wrath of the SNA interests ... resulting in her being removed from the position. It didn't do the SNA interests any good ... since Amadeus went with x.25 anyway.
misc. past posts mentioning Amadeus
https://www.garlic.com/~lynn/2001g.html#49 Did AT&T offer Unix to Digital Equipment in the 70s?
https://www.garlic.com/~lynn/2001g.html#50 Did AT&T offer Unix to Digital Equipment in the 70s?
https://www.garlic.com/~lynn/2001h.html#76 Other oddball IBM System 360's ?
https://www.garlic.com/~lynn/2003d.html#67 unix
https://www.garlic.com/~lynn/2003n.html#47 What makes a mainframe a mainframe?
https://www.garlic.com/~lynn/2004b.html#6 Mainframe not a good architecture for interactive workloads
https://www.garlic.com/~lynn/2004b.html#7 Mainframe not a good architecture for interactive workloads
https://www.garlic.com/~lynn/2004m.html#27 Shipwrecks
https://www.garlic.com/~lynn/2004o.html#23 Demo: Things in Hierarchies (w/o RM/SQL)
https://www.garlic.com/~lynn/2004o.html#29 Integer types for 128-bit addressing
https://www.garlic.com/~lynn/2005f.html#22 System/360; Hardwired vs. Microcoded
https://www.garlic.com/~lynn/2005p.html#8 EBCDIC to 6-bit and back
https://www.garlic.com/~lynn/2006o.html#4 How Many 360/195s and 370/195s were shipped?
https://www.garlic.com/~lynn/2006r.html#9 Was FORTRAN buggy?
https://www.garlic.com/~lynn/2006y.html#14 Why so little parallelism?
https://www.garlic.com/~lynn/2007d.html#19 Pennsylvania Railroad ticket fax service
https://www.garlic.com/~lynn/2007e.html#52 US Air computers delay psgrs
https://www.garlic.com/~lynn/2007h.html#12 The Perfect Computer - 36 bits?
https://www.garlic.com/~lynn/2007k.html#72 The top 10 dead (or dying) computer skills
https://www.garlic.com/~lynn/2007o.html#59 ACP/TPF
https://www.garlic.com/~lynn/2007p.html#45 64 gig memory
https://www.garlic.com/~lynn/2008c.html#53 Migration from Mainframe to othre platforms - the othe bell?
https://www.garlic.com/~lynn/2008i.html#19 American Airlines
https://www.garlic.com/~lynn/2008i.html#34 American Airlines
https://www.garlic.com/~lynn/2008p.html#41 Automation is still not accepted to streamline the business processes... why organizations are not accepting newer technologies?
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Mission Control & Air Cooperation Date: 2 July, 2009 Blog: Disciples of Boyd's Strategyre:
In Boyd's Organic Design for Command and Control ... he would contrast the (US) rigid top-down command and control infrastructure with Guderian's verbal orders only.
Guderian, as part of promoting "on the spot" decision making issued verbal orders only as promoting the local person not having to worry about after-action monday afternoon quarterbacks (provide relatively loose strategic direction with maximum freedom for local tactical decisions).
He would contrast that with the rigid top-down command and control infrastructure inherited from WW2. His explanation was that at entry to WW2, the requirement was to deploy enormous numbers with little or no training. In order to leverage the scarce available skilled resources, a rigid top-down command and control structure was created with battle plans based on massive logistics and resource management.
In the 80s, Boyd would observe that this was starting to adversely affect US corporations, as former officers, that received their training in large organization management in the army, were starting to populate upper corporate executive levels.
misc. past posts mentioning Boyd &/or OODA-loops
https://www.garlic.com/~lynn/subboyd.html#boyd
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: what is mortgage-backed securities? Date: 2 July, 2009 Blog: Equity Marketswhat is mortgage-backed securities? How do they work in U.S. Financial systems? Who benefits from this new financial development.
....
unregulated, non-depository loan originators were using securitization as source of funds. they could buy triple-A ratings for the securities and sell them off. as a result they no longer had to care about quality of the loan and/or qualification of the borrower.
The Man Who Beat The Shorts
http://www.forbes.com/forbes/2008/1117/114.html
from above:
Watsa's only sin was in being a little too early with his prediction
that the era of credit expansion would end badly. This is what he said
in Fairfax's 2003 annual report: "It seems to us that securitization
eliminates the incentive for the originator of [a] loan to be credit
sensitive. Prior to securitization, the dealer would be very concerned
about who was given credit to buy an automobile. With securitization,
the dealer (almost) does not care."
... snip ...
Bernanke Says Crisis Damage Likely to Be Long-Lasting
http://www.bloomberg.com/apps/news?pid=20601087&sid=arpJXeelvfY4&refer=home
from above (something of an understatement):
Bernanke said the packaging and sale of mortgages into securities
"appears to have been one source of the decline in underwriting
standards" because originators have less stake in the risk of a loan.
... snip ...
Evil Wall Street Exports Boomed With 'Fools' Born to Buy Debt
https://www.bloomberg.com/news/articles/2008-10-27/evil-wall-street-exports-boomed-with-fools-born-to-buy-debt
from above:
The bundling of consumer loans and home mortgages into packages of
securities -- a process known as securitization -- was the biggest
U.S. export business of the 21st century. More than $27 trillion of
these securities have been sold since 2001, according to the
Securities Industry Financial Markets Association, an industry trade
group. That's almost twice last year's U.S. gross domestic product of
$13.8 trillion.
... snip ...
From Glass-Steagall (Pecora) hearings, from pg. 7281
BROKERS' LOANS AND INDUSTRIAL DEPRESSION
For the purpose of making it perfectly clear that the present
industrial depression was due to the inflation of credit on brokers'
loans, as obtained from the Bureau of Research of the Federal Reserve
Board, the figures show that the inflation of credit for speculative
purposes on stock exchanges were responsible directly for a rise in
the average of quotations of the stocks from sixty in 1922 to 225 in
1929 to 35 in 1932 and that the change in the value of such Stocks
listed on the New York Stock Exchange went through the same identical
changes in almost identical percentages.
... snip ...
there is a correspondence between the speculation in the real-estate market leveraging (ARM) loans from non-depository institutions (which used securitization as source of funds) and the speculation in the '20s stock market using brokers' loans.
Speculators found no-down, no-documentation, 1%, interest-only payment ARMs quite attractive since the carrying cost was less than the real-estate inflation rate in many parts of the country.
25 People to Blame for the Financial Crisis; Phil Gramm
http://content.time.com/time/specials/packages/article/0,28804,1877351_1877350_1877330,00.html
from above:
He played a leading role in writing and pushing through Congress the
1999 repeal of the Depression-era Glass-Steagall Act, which separated
commercial banks from Wall Street. He also inserted a key provision
into the 2000 Commodity Futures Modernization Act that exempted
over-the-counter derivatives like credit-default swaps from regulation
by the Commodity Futures Trading Commission. Credit-default swaps took
down AIG, which has cost the U.S. $150 billion thus far.
... snip ...
as result of repeal of Glass-Steagall, unregulated investment banking arms of regulated depository institutions were buying up these triple-A rated toxic securities and carrying them off-balance; aka regulated depository institutions were providing funds for these instruments but by circuitous route skirting traditional regulations.
Bank's Hidden Junk Menaces $1 Trillion Purge
>http://www.bloomberg.com/apps/news?pid=newsarchive&sid=akv_p6LBNIdw&refer=home
from above:
So investors betting for quick solutions to the financial crisis could
be disappointed. The tangled web that banks wove over the years will
take a long time to undo.
At the end of 2008, for example, off-balance-sheet assets at just the
four biggest U.S. banks -- Bank of America Corp., Citigroup Inc.,
JPMorgan Chase Co. and Wells Fargo Co. -- were about $5.2 trillion,
according to their 2008 annual filings.
... snip ...
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Average Comp This Year At Top Firm Estimated At $700,000 Date: 2 July, 2009 Blog: Greater IBMAverage Comp This Year At Top Firm Estimated At $700,000
from above:
During these difficult times (financially and politically), executives
at firms like Goldman Sachs are understandably keen to downplay what
bonuses may look like come this year-end.
... snip ...
The Fed's Too Easy on Wall Street
http://www.businessweek.com/stories/2008-03-19/the-feds-too-easy-on-wall-streetbusinessweek-business-news-stock-market-and-financial-advice
from above:
Here's a staggering figure to contemplate: New York City securities
industry firms paid out a total of $137 billion in employee bonuses
from 2002 to 2007, according to figures compiled by the New York State
Office of the Comptroller. Let's break that down: Wall Street honchos
earned a bonus of $9.8 billion in 2002, $15.8 billion in 2003, $18.6
billion in 2004, $25.7 billion in 2005, $33.9 billion in 2006, and
$33.2 billion in 2007.
... snip ...
some part of the $700B wallstreet bailout possibly goes to replenish the $137B sucked out of the infrastructure (as reward for their part in creating the current situation).
... and article from early this year regarding 2008:
Bailed-Out Banks Dole Out Bonuses; Goldman Sachs, CitiGroup, Others
Mum on How They Are Using TARP Cash
http://abcnews.go.com/WN/Business/story?id=6498680&page=1
from above:
Goldman Sachs, which accepted $10 billion in government money, and
lost $2.1 billion last quarter, announced Tuesday that it handed out
$10.93 billion in benefits, bonuses, and compensation for the year.
... snip ...
part of the story for 2008 was that changing accounting lost the month of Dec. where all sorts of things supposedly happened.
In the congressional session that passed the repeal of Glass-Steagall, the financial industry made $250m in contributions, in the last congressional sesssion that passed TARP, the financial industry made $2B in contributions (in aggregate there was $5b in contributions during the period).
more recent article:
Lobbyists on a Roll: Gutting Reform on Banking, Energy, and Health
Care
http://www.huffingtonpost.com/arianna-huffington/lobbyists-on-a-roll-gutti_b_220521.html
then there is this article
The Great American Bubble Machine
http://www.rollingstone.com/politics/story/28816321/the_great_american_bubble_machine
recent item with more articles from rolling stone on the subject
https://www.garlic.com/~lynn/2009j.html#21 The Big Takeover
misc. past posts mentiong Fed's Too Each on Wall Street:
https://www.garlic.com/~lynn/2009.html#73 CROOKS and NANNIES: what would Boyd do?
https://www.garlic.com/~lynn/2009.html#80 Are reckless risks a natural fallout of "excessive" executive compensation ?
https://www.garlic.com/~lynn/2009b.html#25 The recently revealed excesses of John Thain, the former CEO of Merrill Lynch, while the firm was receiving $25 Billion in TARP funds makes me sick
https://www.garlic.com/~lynn/2009b.html#41 The subject is authoritarian tendencies in corporate management, and how they are related to political culture
https://www.garlic.com/~lynn/2009b.html#45 The recently revealed excesses of John Thain, the former CEO of Merrill Lynch, while the firm was receiving $25 Billion in TARP funds makes me sick
https://www.garlic.com/~lynn/2009b.html#49 US disaster, debts and bad financial management
https://www.garlic.com/~lynn/2009b.html#57 Credit & Risk Management ... go Simple ?
https://www.garlic.com/~lynn/2009b.html#59 As bonuses...why breed greed, when others are in dire need?
https://www.garlic.com/~lynn/2009d.html#0 PNC Financial to pay CEO $3 million stock bonus
https://www.garlic.com/~lynn/2009d.html#3 Congress Set to Approve Pay Cap of $500,000
https://www.garlic.com/~lynn/2009e.html#17 Why is everyone talking about AIG bonuses of millions and keeping their mouth shut on billions sent to foreign banks?
https://www.garlic.com/~lynn/2009e.html#36 Architectural Diversity
https://www.garlic.com/~lynn/2009g.html#31 OODA-loop obfuscation
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: A Complete History Of Mainframe Computing Newsgroups: alt.folklore.computers Date: Fri, 03 Jul 2009 06:18:20 -0400Patrick Scheible <kkt@zipcon.net> writes:
in ha/cmp scale-up
https://www.garlic.com/~lynn/subtopic.html#hacmp
then the scale-up activity got transferred and we were told that we couldn't work on anything with more than four processors.
within weeks after the transfer ... some press releases:
https://www.garlic.com/~lynn/2001n.html#6000clusters1 ... scientific and technical only
https://www.garlic.com/~lynn/2001n.html#6000clusters2 ... caught by surprise
recent items in the trend:
News Story DARPA Wants a 19in Super-Efficient Supercomputer
http://news.slashdot.org/story/09/06/27/2118232/DARPA-Wants-a-19-Super-Efficient-Supercomputer
Supercomputers Lose Glamour, Price Tag
http://www.pcworld.com/businesscenter/article/167504/supercomputers_lose_glamour_price_tag.html
reference to writing several papers in early 1985 about cluster
configuration "densely" packing as many microprocessors as possible in
racks (major problem was heat and cooling)
https://www.garlic.com/~lynn/2004m.html#17 mainframe and microprocessor
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: what is mortgage-backed securities? Date: 3 July, 2009 Blog: Equity Marketsre:
article referencing what happened when the market started to realize that it was possible to buy triple-A ratings:
Barney Frank Backs Off
http://www.forbes.com/2009/05/04/barney-frank-defers-opinions-contributors-regulation.html
from above
The crisis did not begin when Lehman failed; it began in the summer of
2007 with the markets' sudden realization that the triple-A ratings on
asset-backed securities were not accurate. The resulting loss of
confidence in ratings was a powerful external shock to the market,
causing a collapse in trading of all asset-backed securities. That
market is still frozen, and the Fed's efforts to revive it through
TALF have not borne fruit.
... snip ...
being able to buy triple-A ratings enormously increased the entities that would deal in the toxic securities and therefor the aggregate amount of money involved (earlier asset-backed security dealings would have had much less effect since there was a big limitation on those that would deal in the instruments and therefor the aggregate amount of money involved)
more recent article regarding the rating agencies (and the consequences of being able to buy triple-A ratings):
Credit Rating Agencies Spared Major Reforms In Obama's Overhaul
http://www.huffingtonpost.com/2009/06/17/credit-rating-agencies-sp_n_217139.html
from above:
They've been called the culprits of the financial crisis but their
role has remained largely unexamined. And they were largely spared any
major reforms in the financial regulatory overhaul announced today by
President Obama.
... snip ...
What Caused the Financial Meltdown?
http://www.claremont.org/publications/crb/id.1620/article_detail.asp
from above:
Still, these loans moved briskly along the financial assembly line --
bankers or mortgage brokers made loans; the loans were sold to
investment bankers who "securitized" them into bond-like securities;
rating agencies like Moody's and Standard & Poor's graded the
different tranches, allowing them to be sold to investors -- banks,
pensions, hedge funds -- who thought they knew what they were buying.
... snip ...
Gut Check Time on Shackling Wall St
http://www.opednews.com/articles/Gut-Check-Time-on-Shacklin-by-Josh-Mitteldorf-090624-264.html
from above:
It could expose how the banks and rating agencies colluded to
transform garbage NINJA (no income, no job, no assets) mortgages into
triple A securities. It could subpoena the barons to show how they
profited personally and turned their eyes as the banks took ever
greater risks, gambling with ever higher levels of borrowed money. It
could make the case for adult supervision.
... snip ...
some older references
How Wall Street Lied to Its Computers
http://bits.blogs.nytimes.com/2008/09/18/how-wall-streets-quants-lied-to-their-computers/
and
Subprime = Triple-A ratings? or 'How to Lie with Statistics' (gone 404 but lives on at the wayback machine)
https://web.archive.org/web/20071111031315/http://www.bloggingstocks.com/2007/07/25/subprime-triple-a-ratings-or-how-to-lie-with-statistics/
misc. other articles
Rating agencies largely spared in Obama overhaul
http://www.reuters.com/article/ousivMolt/idUSTRE55G5SJ20090617
Lobbyists on a Roll: Gutting Reform on Banking, Energy, and Health Care
http://www.huffingtonpost.com/arianna-huffington/lobbyists-on-a-roll-gutti_b_220521.html
Overhaul Leaves Rating Agencies Largely Untouched
http://compliancex.typepad.com/compliancex/2009/06/overhaul-leaves-rating-agencies-largely-untouched.html
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: A Complete History Of Mainframe Computing Newsgroups: alt.folklore.computers Date: Sat, 04 Jul 2009 09:11:41 -0400Brian Boutel <fake@fake.nz> writes:
in the discussion about 701 and 650 ... 701 was "defense calculator" ... and only 19 sold ... while 650 was something of a more sophisticated tabulating equipment ... used in conjunction with other card tabulating equipment (and sold 2000). one might conjecture that increasing sophistication of 650 and follow-ons, "mainframe" might be used to differentiate from the other card tabulating equipment that would also be around.
recent 701 & 650 thread
https://www.garlic.com/~lynn/2009h.html#12 IBM Mainframe: 50 Years of Big Iron Innovation
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: My "Green Screen" IBMLink is still working Newsgroups: bit.listserv.ibm-main Date: Sat, 04 Jul 2009 14:54:52 -0400barry@MXG.COM (Barry Merrill) writes:
post with some of the analysis
https://www.garlic.com/~lynn/2001m.html#19 3270 protocol
as noted in the above ... TSO didn't care since they never really claimed to be interactive computing or considered subsecond response time.
japan did do (ascii, glass teletype) 3101/topaz ... old reference
going into some references
https://www.garlic.com/~lynn/2007e.html#15
we had some number of early 3101 "-1" ... and were looking to get copy of the ROM for "-2" and burning our own ROMs to field upgrade from "-1" to "-2".
prior to getting 3101 at home, I had cdi miniterm ... some old pictures
including home cdi miniterm and home 3101 (not a very good picture)
https://www.garlic.com/~lynn/lhwemail.html#oldpicts
one of the pictures shows an old "HYPER" 3270 logon screen.
this was project to move 300 people from the IMS group out of STL to an offsite bldg with their 3270 CMS service back to STL datacenter. They had looked at doing "remote" 3270 ... but the human factors were intolerable.
I did HYPERchannel device driver for them ... basically channel extender over T1 microwave link ... with 300 "local" 3270s at the remote end. The transmission time wasn't seriously affected ... but a side-effect of moving the 3274 controllers directly off the mainframe channels, resulted in overall 10-15% increased system thruput ... i.e. the HYPERchannel controllers had significantly lower channel busy for the same amount of 3270 data ... vis-a-vis 3274 controllers, the significant reduction in (3270) channel busy resulted in overall system thruput increase.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: How can we stop Credit card FRAUD? Date: 5 July, 2009 Blog: Financial Crime Risk, Fraud and SecurityWe had been asked to consult with small client/server startup that wanted to do payment transactions on their server, they had also invented this technology called SSL they wanted to use; the result is now frequently called "electronic commerce".
Somewhat as a result, in the mid-90s we were asked to participate in
the X9A10 financial standard working group which had been given the
requirement to preserve the integrity of the financial infrastructure
for all retail payments (i.e. ALL as in, debit, credit,
stored-value, ACH, gift/merchant card, point-of-sale, unattended,
face-to-face, transit turnstyle, internet, aka ALL). As part of that
effort, there was end-to-end threat & vulnerability of the various
environments. The result was the X9.59 financial standard (to address
preserving the integrity of the financial infrastructure for ALL
retail payments) ... some references
https://www.garlic.com/~lynn/x959.html#x959
We've used a number of metaphors to characterize the current paradigm:
• security proportional to risk metaphor; in the current paradigm, the value of the information to the merchant is the profit on the transaction (possibly a couple dollars) and the value of the information to the processor can be a few cents per transaction ... while the value of the information to the crooks can be the credit limit and/or account balance (the crooks attacking the infrastructure may be able to outspend the merchant & processor defenders by a factor of one hundred times)
• dual-use vulnerability metaphor; in the current paradigm, the knowledge of the account number may be sufficient to perform a fraudulent transaction (effectively authentication, as such it needs to be kept confidential and never divulged anywhere) ... while at the same time the account number needs to be readily available for a large number of business processes. The conflicting requirements (never divulged and at the same time readily available) has led to comments that even if the planet was buried under miles of information hiding encryption, it still couldn't prevent information leakage.
A dual-use account paradigm analogy would be a userid/password scheme ... where there is no password and the userid must be made to do double duty ... used for lots & lots of processes (requiring it to be readily available) and at the same time used for authentication (requiring it to be kept confidential and never divulged).
An example would be requiring the userid to be publicly available for email purposes (i.e. email wouldn't be able to work w/o knowledge of the userid) ... but at the same time, knowledge of the userid would allow anybody to take over an account and impersonate the valid owner.
So all email headers (containing a userid) have to be kept encrypted and completely hidden so that it is never divulged ... but at the same time ... people needing to send you email have to know your userid (w/o knowing your userid)
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Mission Control & Air Cooperation -- Part I Date: 5 July, 2009 Blog: Boydre:
For the fun of it: ... post from april
https://www.garlic.com/~lynn/2009g.html#16 USAF officers slammed for pranging Predators on manual
for the fun of it ...
USAF officers slammed for pranging Predators on manual
http://www.theregister.co.uk/2009/04/29/young_usaf_predator_pilot_officer_slam/
from the above:
A senior Pentagon official has delivered a stinging attack on the US
Air Force, saying that its philosophy of using fully qualified human
pilots to handle unmanned aircraft at all times has resulted in
unnecessary, expensive crashes. By contrast, US Army drones with
auto-landing equipment and cheaply-trained operators have an enviable
record
... snip ...
... and ...
The US Army has a differing philosophy: it's "Sky Warrior" variant of
the Predator is intended to land itself automatically, and the
present-day Shadow has such kit already. Army drones are controlled by
noncomissioned tech specialists who, while fully trained and qualified
for their job, have no airborne stick time in regular aircraft. They
are always in theatre with the rest of the troops.
... snip ...
almost a Boyd'ism
https://www.garlic.com/~lynn/subboyd.html
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Usability and security gurus agree that masked passwords should go Date: 5 July, 2009 Blog: Computer Security and Forensicsre:
The article also references possibly higher security for banking
transactions ... this is recent long-winded, archived post about
encryption, data breaches, financial transactions, transaction
standards, etc
https://www.garlic.com/~lynn/2009j.html#33
slightly related (archived) discussion from crypto mailing list
mentioning pin/passwords being vulnerable to keyloggers. this has been
well known for at least a decade ... in part, in the late 90s there
was work on EU "finread" standard ... which included a "trusted"
PIN-pad as countermeasure to keyloggers:
https://www.garlic.com/~lynn/2009j.html#31
some discussion of RFC 2289 ... one-time password ... using iterative hash. in theory this was usable at internet cafe ... with some sort of static storage that the user carried with them. passphrases are somewhat more common in association with encryption/decryption (key being function of the passphrase).
in theory the passphrase (at internet cafe, in effect something you know authentication) doesn't do any good w/o the corresponding static storage (in effect something you have authentication) containing the encrypted value.
the problem is compromises of machine at internet cafe can capture
both the passphrase as well as the contents of the static storage
(nominal multi-factor authentication is assumed to be more secure when
the different factors have different vulnerabilities, this is
invalidated when *all* factors may be subject to common static data
capture).
https://www.garlic.com/~lynn/2003m.html#1
https://www.garlic.com/~lynn/2003m.html#50
https://www.garlic.com/~lynn/2005l.html#8
https://www.garlic.com/~lynn/2005o.html#0
https://www.garlic.com/~lynn/2005t.html#28
https://www.garlic.com/~lynn/2005t.html#31
https://www.garlic.com/~lynn/2006d.html#41
https://www.garlic.com/~lynn/2006v.html#46
https://www.garlic.com/~lynn/2007u.html#59
as in above discussion, rfc 2289 can also be vulnerable to "active" MITM attacks, where the intermediary spoofs a very low "iteration" number ... and then has access to all iterations large than the spoofed value.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Revisiting the Five-Minute Rule Newsgroups: alt.folklore.computers Date: Sun, 05 Jul 2009 12:05:27 -0400Revisiting the Five-Minute Rule
from above:
In 1987, Gray and Putzolu speculated 20 years into the future and
anticipated a "five-hour rule" for RAM and disks. For 1KB records,
prices and specifications typical in 2007 suggest 20,978 seconds, or
just under six hours. Their prediction was amazingly accurate.
... snip ...
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Neuromancer turns 25: What it got right, what it got wrong Newsgroups: alt.folklore.computers Date: Sun, 05 Jul 2009 12:07:32 -0400The Technology of Neuromancer After 25 Years
from above:
What Gibson introduced was the idea of a global network of millions of
computers, which he described in astonishing detail--though the World
Wide Web, as we know it today, was still more than a decade away.
... snip ...
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: How can we stop Credit card FRAUD? Date: 5 July, 2009 Blog: Financial Crime Risk, Fraud and Securityre:
oh, paper from last fall from Kansas City Fed:
Can Smart Cards Reduce Payments Fraud and Identity Theft?
http://www.kansascityfed.org/Publicat/ECONREV/PDF/3q08Sullivan.pdf
and some archived posts in the discussion:
https://www.garlic.com/~lynn/2008p.html#11
https://www.garlic.com/~lynn/2008p.html#14
https://www.garlic.com/~lynn/2008p.html#15
https://www.garlic.com/~lynn/2008p.html#18
https://www.garlic.com/~lynn/2008p.html#19
https://www.garlic.com/~lynn/2008p.html#44
https://www.garlic.com/~lynn/2008p.html#49
https://www.garlic.com/~lynn/2008p.html#55
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Specifications Newsgroups: alt.folklore.computers Date: Mon, 06 Jul 2009 14:14:55 -0400Patrick Scheible <kkt@zipcon.net> writes:
took a month
the 20th anniv. edition comes out in a couple weeks:
A Peace to End All Peace, 20th Anniversary Edition: The Fall of the
Ottoman Empire and the Creation of the Modern Middle East
https://www.amazon.com/Peace-End-All-20th-Anniversary/dp/0805088091/
the original appeared to have been in part because of (then) recently declassified british documents.
the book pretty much lays out that the whole mid-east is the way it is today ... because of how british set it up in the 20s. In that sense ... recent events are pretty much the US going along with the way the British put it all together.
from last year ... there was report/claim projecting that use would exceed new (oil deposit) discoveries around 2011 ... recent economic troubles and downturn in activity may push that out a few years (but resulting in increasing supply/demand issues modulo things like brazil's ethanol).
misc. year old posts&threads (mentioning oil) from last year:
https://www.garlic.com/~lynn/2008c.html#17 Toyota Sales for 2007 May Surpass GM
https://www.garlic.com/~lynn/2008d.html#79 was: 1975 movie "Three Days of the Condor" tech stuff
https://www.garlic.com/~lynn/2008e.html#7 was: 1975 movie "Three Days of the Condor" tech stuff
https://www.garlic.com/~lynn/2008e.html#17 MAINFRAME Training with IBM Certification and JOB GUARANTEE
https://www.garlic.com/~lynn/2008e.html#23 was: 1975 movie "Three Days of the Condor" tech stuff
https://www.garlic.com/~lynn/2008f.html#56 China overtakes U.S. as top Web market
https://www.garlic.com/~lynn/2008h.html#3 America's Prophet of Fiscal Doom
https://www.garlic.com/~lynn/2008h.html#11 The Return of Ada
https://www.garlic.com/~lynn/2008h.html#15 The Return of Ada
https://www.garlic.com/~lynn/2008h.html#19 The Return of Ada
https://www.garlic.com/~lynn/2008i.html#56 The Price Of Oil --- going beyong US$130 a barrel
https://www.garlic.com/~lynn/2008i.html#98 dollar coins
https://www.garlic.com/~lynn/2008j.html#80 dollar coins
https://www.garlic.com/~lynn/2008k.html#6 dollar coins
https://www.garlic.com/~lynn/2008k.html#16 dollar coins
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Replace the current antiquated credit card system Date: 7 July, 2009 Blog: Payment Systems Networkpaper last fall from Kansas City Fed:
Can Smart Cards Reduce Payments Fraud and Identity Theft?
http://www.kansascityfed.org/Publicat/ECONREV/PDF/3q08Sullivan.pdf
and some archived posts in the discussion:
https://www.garlic.com/~lynn/2008p.html#11
https://www.garlic.com/~lynn/2008p.html#14
https://www.garlic.com/~lynn/2008p.html#15
https://www.garlic.com/~lynn/2008p.html#18
https://www.garlic.com/~lynn/2008p.html#19
https://www.garlic.com/~lynn/2008p.html#44
https://www.garlic.com/~lynn/2008p.html#49
https://www.garlic.com/~lynn/2008p.html#55
The paper mentions X9.59 financial transaction standard.
We had been brought in to consult with small client/server startup that wanted to do payment transactions on their server; they had also invented this technology called SSL; the result is now frequently called "electronic commerce".
Somewhat as a result, in the mid-90s we were asked to participate in
the x9a10 financial standard working group which had been given the
requirement to preserve the integrity of the financial infrastructure
for all retail payments (ALL as in debit, credit, stored-value, gift
card, ACH, point-of-sale, face-to-face, unattended, cellphone, transit
turnstyle, low-value, high-value; wireless, contact, contactless, aka
ALL). The result was the x9.59 financial transaction standard
https://www.garlic.com/~lynn/x959.html#x959
Part of the effort was to do detailed, end-to-end threat and vulnerability analysis of the various environments ... identifying various things including lost/stolen, skimming, evesdropping, data breaches, insiders, external attacks, and numerous more.
Disclaimer ... in previous life, I had several offices and labs in the
los gatos lab. ... mentioned in this wiki reference about origins of
magnetic stripe:
https://en.wikipedia.org/wiki/Magnetic_stripe
as well as this reference regarding development of early ATM machines
https://en.wikipedia.org/wiki/IBM_3624
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: OT Kodachrome film discontinued Newsgroups: alt.folklore.computers Date: Tue, 07 Jul 2009 10:22:34 -0400Quadibloc <jsavard@ecn.ab.ca> writes:
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: How can we stop Credit card FRAUD? Date: 7 July, 2009 Blog: Financial Crime Risk, Fraud and Securityre:
a couple yrs ago, there was a long-running, long-winded thread in the crypto mailing list ... started out with statement that the banks' profit actually increases as the fraud goes up ... so they have little incentive to reduce the fraud (with the merchants bearing the cost). maximize the bottom line theoretically is maximize fraud to just less than point where consumers will stop using the cards.
some archived posts in that thread ... observing that there were some
chip deployments in the early part of this decade ... which relatively
rapidly evaporated. there were comments about issues with technology
change-over costs ... however, it seemed to be concern about the costs
of some number of failed deployments ... (as opposed to costs of
single successful deployment). there were also issues about fragmented
(chip) solutions ... i.e. not a single, interoperable solution across
all possible payment environments:
https://www.garlic.com/~lynn/aadsm27.htm#31 The bank fraud blame game
https://www.garlic.com/~lynn/aadsm27.htm#32 The bank fraud blame game
https://www.garlic.com/~lynn/aadsm27.htm#33 The bank fraud blame game
https://www.garlic.com/~lynn/aadsm27.htm#34 The bank fraud blame game
https://www.garlic.com/~lynn/aadsm27.htm#35 The bank fraud blame game
https://www.garlic.com/~lynn/aadsm27.htm#37 The bank fraud blame game
https://www.garlic.com/~lynn/aadsm27.htm#38 The bank fraud blame game
https://www.garlic.com/~lynn/aadsm27.htm#39 a fraud is a sale, Re: The bank fraud blame game
https://www.garlic.com/~lynn/aadsm27.htm#40 a fraud is a sale, Re: The bank fraud blame game
https://www.garlic.com/~lynn/aadsm27.htm#41 The bank fraud blame game
https://www.garlic.com/~lynn/aadsm27.htm#42 The bank fraud blame game
https://www.garlic.com/~lynn/aadsm27.htm#43 a fraud is a sale, Re: The bank fraud blame game
i.e. part of the theme was that while financial institutions have control over the current payment card infrastructure, the fees (paid by merchants) are structured such that financial institutions have greater profit from transactions with higher fraud rates. a conjecture was that this might result in conflict of interest ... where financial infrastructure have less motivation to significantly reduce fraud as long as the profits are much higher.
Some of this has been somewhat alluded to in the Wal-Mart/merchant case ... recent reference
MasterCard Puts the 13-Year-Old Wal-Mart Case in the Rear-View Mirror
http://www.digitaltransactions.net/newsstory.cfm?newsid=2256
with conjecture that possible motivation for preference given to "signature-debit" over "pin-debit" was that "signature-debit" has 15 times the fraud rate of "pin-debit" ... along with corresponding higher (merchant interchange) fees and profits.
Study: Signature Debit Fraud Runs 15 Times Higher Than on PIN Debit
http://www.digitaltransactions.net/newsstory.cfm?newsid=738
there have also been some number of recent articles about various merchants refusing to accept signature-debit and other payment cards that have much higher merchant interchange fees.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Replace the current antiquated credit card system Date: 7 July, 2009 Blog: Payment Systems Networkre:
In the AADS patent portfolio (even chugging along long after we left;
they are all assigned patents and we have no interest):
https://www.garlic.com/~lynn/aadssummary.htm
there is integration of 3-factor authentication paradigm ... misc.
posts
https://www.garlic.com/~lynn/subintegrity.html#3factor
• something you have
• something you know
• something you are
In the "AADS" scenario for X9.59 financial transactions .. there is the concept of security proportional to risk ... where the amount/level of authentication can be proportional to the transaction value.
The idea of dynamic/static comes from analysis of class of replay attacks ... can a crook create a successful fraudulent transaction from information from previous transactions (skimming, evesdropping, data breaches, etc).
In the AADS scenario ... it might be possible to use a chipcard for a low-value transaction (just dynamic data produced by the chip) ... but w/o additional levels of authentication. Higher value transactions may require additional levels of authentication. AADS scenario does have concept of online transactions ... so that amount of fraud, even in low-value scenario can be bounded by deactivating the account number.
there is some x-over with (linkedin) Financial Crime Risk, Fraud and
Security group in "How can we stop Credit card FRUAD?" thread ... part
of it archived here:
https://www.garlic.com/~lynn/2009j.html#41
https://www.garlic.com/~lynn/2009j.html#46
https://www.garlic.com/~lynn/2009j.html#50
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: A Complete History Of Mainframe Computing Newsgroups: alt.folklore.computers Date: Tue, 07 Jul 2009 13:43:25 -0400re:
bits & pieces from ha/cmp project marketing study we had done in fall of 89
Estimated 1988-1992 WW Installed Base Category 1988 1992 CGR Supercomputers 350 1000 22% Mainframes 6000 12000 6% minisupers 2200 11000 41% superminis 300,000 900,000 20% workstations 370,000 2,750,000 52% Workstation Unit Shipments Worldwide 1986-1993 (000s) 1986 50 1987 100 1988 200 1989 300 1990 450 1991 650 1992 950 1993 1200misc. past posts mentioning ha/cmp
then "supercomputers" turned into large collections of "workstation" technology.
...
and misc. DEC "mainframe" news tidbits from Oct89:
DEC is planning a big coming-out party on Tuesday
- first line of mainframe computers ... VAX 9000
- IBM is expected to announce its own mainframe
. "They're deliberately trying to steal our thunder ....
maybe we should take it as a compliment" -DEC executive
- Digital has spent almost $1 billion developing new technology
. promises a new approach ... a decentralized network
. air-cooled mainframe
. It's been a long time coming
- A full family will be announced
. 4 models aimed squarely at IBM's commercial customers
. volume shipments won't begin until next year
- Model 210 will be the first available
. Appeals to technical and scientific buyers
. Optional "Supercharger" vector processor
- A spoiler, nimble Tandem, jumped into the fray earlier this week
. IBM seems more worried about DEC
Mainframe market .. $40 billion
- nearly every big company needs one
- IBM has dominated ... that doesn't scare DEC (world's 2nd largest mfger)
- Challengers have a big price advantage
. DEC: $1.24-4.4 million, and up (half the price of IBM)
. Tandem: Pricing is just as aggressive
- Competition hits IBM at a difficult time
. current mainframe line is starting to show its age
. New 3090's will boost performance only 8-10%
. New generation not expected from IBM until 1991
- No one expects competitors to deliver a knock-out punch to IBM
. IBM has a near monopoly on mainframes (est. 70%)
. IBM is 5-times the size of DEC; 40-times the size of Tandem
. IBM customers are the largest corporations in the world
- Kenneth Olsen
. "We're not going to walk in and replace a company's corporate
accounting system if it's already running on an IBM mainframe"
- DEC will target growing market segments
. online transaction processing (Tandem specializes in this market)
. customers who have both IBM and DEC equipment
--
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Memories Of CompuServe, Prodigy And Other Dinosaurs Newsgroups: alt.folklore.computers Date: Tue, 07 Jul 2009 14:05:58 -0400Memories Of CompuServe, Prodigy And Other Dinosaurs
from above:
Believe it or not, dial-up access to the Internet still exists and up
until last week so did CompuServe, one of the few remaining service
providers and a pioneer of social networking.
... snip ...
some old pictures ... included cdi miniterm (at home in the 70s, used
for dial-up)
https://www.garlic.com/~lynn/lhwemail.html#oldpicts
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: A Complete History Of Mainframe Computing Newsgroups: alt.folklore.computers Date: Tue, 07 Jul 2009 14:29:51 -0400Patrick Scheible <kkt@zipcon.net> writes:
there is some implication that superminicomputers might have (programming/software) compatibility with minicomputers (DEC) and minisupercomputers might have compatibility with supercomputers (cray or others)
this old post has extract from Jan88 report/study
https://www.garlic.com/~lynn/2001b.html#55 Why SMP at all anymore?
which seems to slip back & forth between minisupers and superminis
Alliant 171 Celerity just shipping Convex 200 ELXSI 80 FPS 365 Gould 6 Multiflow 5 Scientific 25 Computing Supertek not shipping yet... snip ...
which lists approx. 850 minisupers (for US at some pt before Jan88 report) ... while ha/cmp fall 1989 marketing study lists 2200 (world wide in 1988) ... aka part of ha/cmp was focused on HA - high availability ... ha/cmp also had cmp cluster scale-up focus.
2200 for mini (small) supercomputers is significantly fewer than the 300,000 for super (large) minicomputers.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Replace the current antiquated credit card system Date: 7 July, 2009 Blog: Payment Systems Networkre:
there is sometimes confusion regarding authentication and identification ... many times payments require authentication ... but don't actually require identification. In fact, at one point, the EU was asking that electronic transactions not require identification (as a privacy issue) ... aka at least names would be removed from payment cards.
we've also periodically observed possible semantic confusion between
"human signature" (indication of having read, understood, approves,
authorizes and/or agrees) and "digital signature" ... possibly because
the two terms both contained the word "signature". we had been called
in to help word-smith the cal. electronic signature legislation
... and the issue with (simple) digital signature not meeting the
requirement for "human" signature was explored in some detail. some
past posts
https://www.garlic.com/~lynn/subpubkey.html#signature
there is also an dual-use vulnerability issue if the same private key
(digital signature) is used both for straight-forward authentication
processes as well as in conjunction with additional procedures for
"electronic signatures" ... part of past, long-winded discussion in
crypto mailing list
https://www.garlic.com/~lynn/aadsm17.htm#57 dual-use digital signature vulnerability
https://www.garlic.com/~lynn/aadsm17.htm#59 dual-use digital signature vulnerability
https://www.garlic.com/~lynn/aadsm18.htm#0 dual-use digital signature vulnerability
https://www.garlic.com/~lynn/aadsm18.htm#1 dual-use digital signature vulnerability
https://www.garlic.com/~lynn/aadsm18.htm#2 dual-use digital signature vulnerability
https://www.garlic.com/~lynn/aadsm18.htm#3 dual-use digital signature vulnerability
https://www.garlic.com/~lynn/aadsm18.htm#4 dual-use digital signature vulnerability
https://www.garlic.com/~lynn/aadsm18.htm#6 dual-use digital signature vulnerability
https://www.garlic.com/~lynn/aadsm18.htm#12 dual-use digital signature vulnerability
https://www.garlic.com/~lynn/aadsm18.htm#13 dual-use digital signature vulnerability
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Replace the current antiquated credit card system Date: 7 July, 2009 Blog: Payment Systems Networkre:
Two things in X9.59 financial transaction standard, 1) it provided for
authentication w/o requiring name/identification and 2) it slightly
tweaked the paradigm so that crooks could no longer utilize
information from skimming, evesdropping, and/or data breaches for the
purposes of fraudulent transactions.
https://www.garlic.com/~lynn/x959.html#x959
We had been tangentially involved with the cal. data breach notification legislation (first in the country) when we were brought in to help word smith the cal. electronic signature legislation. several of the parties involved in electronic signature were also involved in privacy and had done detailed, in-depth consumer privacy surveys. The number one issue in the privacy surveys was "identity theft" ... most notably fraudulent financial transactions as a result of various kinds of data breaches. At the time, little or nothing seemed to be done about the problem ... so they apparently felt that the publicity from the breach notifications might motivate corrective action.
Note that x9.59 standard did nothing about preventing skimming, evesdropping and/or data breaches ... but it did prevent the fraudulent transactions that were the result of such exploits (i.e. it removed the financial fraud threat and the primary motivation for crooks).
Now, the primary use of SSL in the world today ... is this earlier electronic commerce thing that we worked on, involved in hiding information about financial transaction information (in order to prevent crooks from being able use the information to perform fraudulent transactions). X9.59 eliminates the ability of crooks to use such information for fraudulent transactions ... and therefor eliminates the need to use SSL for that purpose
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: How can we stop Credit card FRAUD? Date: 9 July, 2009 Blog: Financial Crime Risk, Fraud and Securityre:
slightly related article from today:
Online fraud hurting e-commerce adoption: Australian Retailers
Association Merchants, not consumers, banks or credit-card providers,
are the hardest hit by online fraud.
http://www.cio.com.au/article/310540/online_fraud_hurting_e-commerce_adoption_australian_retailers_association?fp=4&fpid=51238
as to the line regarding the benefit of the transaction information to
the merchant can be a couple dollars (per transaction) and the benefit
of the transaction information to the processors can be a few cents
(per transaction) ... but the transaction information to the crook
(say in a data breach) can be the credit limit or account balance
(effectively a kind of replay attack) ... as a result the
attacker/crooks may be able to outspend by a factor of 100 times
attacking the system ... as the defenders can afford to spend ... post
from 2001:
https://www.garlic.com/~lynn/2001h.html#61
a theme that has been repeated several times since ... a few recent:
https://www.garlic.com/~lynn/2009j.html#11 Is anyone aware of a system that offers three layers of security and ID protection for online purchases or even over the counter POS purchases?
https://www.garlic.com/~lynn/2009j.html#13 PCI SSC Seeks Input on Security Standards
https://www.garlic.com/~lynn/2009j.html#33 IBM touts encryption innovation
and another article from today:
E-commerce sites still at risk from man in the middle attacks
http://www.computerweekly.com/Articles/2009/07/09/236831/e-commerce-sites-still-at-risk-from-man-in-the-middle.htm
from above:
No matter what type of authentication, from basic to the highly
encrypted, or whether organisations use password-based
or two-factor authentication, their websites are vulnerable
... snip ...
as referred to about the work in the X9A10 financial standard working group ... there was a look at the end-to-end threat and vulnerability across a lot of different environments and financial transactions. There was nothing done in the resulting x9.59 financial transaction standard to prevent such exploits ... but what X9.59 did was eliminate the major motivation for such exploits (the ability to use the information for fraudulent financial transactions).
With regard to SSL ... lots of past posts related to early work we had
done on "electronic commerce" involving SSL
https://www.garlic.com/~lynn/subpubkey.html#sslcert
various past archived posts mentioning MITM-attacks
https://www.garlic.com/~lynn/subintegrity.html#mitmattack
As previously mentioned we had been called in to consult with small client/server startup that wanted to do payment transactions on their server; they had also invented a technology called SSL they wanted to use; the result is now frequently referred to as electronic commerce. As part of that effort we had to do detail look at how SSL was being implemented and used ...as well as these new things calling themselves certification authorities. One of the things that happened is nearly immediately lots of merchants found that SSL was significantly cutting their thruput and performance ... and cut back in how it was used (invalidating some basic assumptions about its ability to provide assurance).
Somewhat as a result of the electronic commerce work, in the mid-90s we were invited to participate in the X9A10 financial standard working group which had been given the requirement to preserve the integrity of the financial infrastructure for all retail payments ... this involved some end-to-end, detailed threat & vulnerability studies of the various environments (aka the ALL requirement). A lot of of the threats and vulnerabilities was from being able to use information from previous transactions (evesdropping, skimming, data breaches, MITM, etc) to perform fraudulent transactions.
X9A10 didn't address preventing evesdropping, skimming, data breaches
issues ... with the x9.59 financial transaction standard ... some
references
https://www.garlic.com/~lynn/x959.html#x959
it addressed slightly tweaking the infrastructure making the information from previous transactions (like account numbers) useless to attackers (for the purpose of doing fraudulent transactions).
Some archived posts from a recent, similar thread in (linkedin)
Payment Systems network
https://www.garlic.com/~lynn/2009j.html#26
https://www.garlic.com/~lynn/2009j.html#29
https://www.garlic.com/~lynn/2009j.html#48
https://www.garlic.com/~lynn/2009j.html#51
https://www.garlic.com/~lynn/2009j.html#55
https://www.garlic.com/~lynn/2009j.html#56
https://www.garlic.com/~lynn/2009j.html#58
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Price Tag for End-to-End Encryption: $4.8 Billion, Mercator Says Date: 9 July, 2009 Blog: Payment Systems Networkre:
a "provisioning" cost issue:
MasterCard Halts Remote POS Security Upgrades
http://www.pcworld.com/businesscenter/article/168106/mastercard_halts_remote_pos_security_upgrades.html
there has been industry "slamming" issue ... where merchants are talked into switching processors ... and existing physical POS terminals (at merchant) are reprogrammed to work with a different processor (issue where POS terminal is supplied by the original processor).
early part of this decade there was look at adding "AADS" capability
to POS terminals ... for a number of new authentication functions
... one being countermeasure to "processor switching" involving
non-merchant owned, processor provided POS terminals. misc. AADS
references
https://www.garlic.com/~lynn/x959.html#aads
In the mid-90s I had semi-facetiously said I was going to take a $500 milspec part, aggressively cost reduce by 2-3 orders of magnitude while improving the integrity ... with a little slight of hand, I got on the EPC RFID cost curve (i.e. chips touted as replacing UPC barcodes on grocery items) but with "dynamic data" and some other functions as opposed to straight static data.
A little later, I was on assurance panel in the TCPA track at the
intel developer's group ... the person running TCPA was in the front
row ... so I somewhat kidded that it was nice to see that TPM design
had been getting simpler over previous couple yrs and was starting
to look at lot more like AADS chip strawman; so he quipped back that I
didn't have to deal with a committee of a couple hundred people
helping me with the (AADS) design (by that time, quantity AADS wafer
cost had per-AADS chip well under 1/10th that of TPM chip). minor
reference:
https://web.archive.org/web/20011109072807/http://www.intel94.com/idf/spr2001/sessiondescription.asp?id=stp%2bs13
Part of this was some experience looking at DRM for the IBM/PC (dating back to shortly after product was announced) ... the extra hardware on IBM/PC motherboard at the time (reasonably probability of zeroization when tampered) was quite formidable.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: A Complete History Of Mainframe Computing Newsgroups: alt.folklore.computers Date: Thu, 09 Jul 2009 17:49:44 -0400hancock4 writes:
which included 3031 (warmed-over 370/158), 3032 (warmed-over 370/168), and 3033 (which started at with 168 wiring diagram mapped to newer chip technology that was 20% faster). At the same time, they took the 158 microcode engine with the 158 integrated channel microcode and created the 303x channel director (basically 158 w/o 370 microcode capability). Then 3031 coupled with 303x channel director was two 158 microcode engines ... one with 370 microcode and no integrated channel microcode and the other with integrated channel microcode and no 370 microcode. 370/168 already used external channel boxes, so it wasn't difficult to adapt it to 303x channel director (158 microcode engine w/o 370 microcode, just the integrated channel microcode).
there was a fiber-optic channel technology that had been kicking around pok for a number of years. one of the rs6000 engineers took the design, tweaked it so it was about ten percent higher transmission rate and used much less expensive, commodity-priced optical drivers. It was released on rs/6000 as SLA (serial-link adapter, including full-duplex operation, put incompatible with mainframe).
The release of ESCON for mainframe was traditional half-duplex channel operation (limited thruput) and latency issues at longer distances.
The SLA engineer then wanted to start work on 800-mbit version of SLA. We took some time to convince him to join the FCS committee instead (he became secratary for the organization ... and main editor of the FCS standards document). We had been doing some amount with LANL in the HiPPI standards committee and with LLNL in the FCS committee. One of the arguments (used with the SLA engineer) was limited uptake for RS/6000 SLA (since it wasn't interoperable with anything else) ... and interoperability was much more important to market rs/6000 was selling into.
Some of the mainframe channel people also got involved in FCS ... and there were periodic heated discussions (some archived in FCS mailing list)... where they were constantly working on layering mainframe half-duplex channel operation above underlying FCS full-duplex operation.
slightly related post mentioning FCS in this post referencing
Jan92 meeting on ha/cmp scale-up
https://www.garlic.com/~lynn/95.html#13
and some amount in this old email on ha/cmp scale-up and
cluster-in-a-box
https://www.garlic.com/~lynn/lhwemail.html#medusa
The "super-duper" channel hardware is FICON ... layered above FCS ...
some reference here:
http://www-03.ibm.com/systems/z/hardware/connectivity/ficon_performance.html
https://en.wikipedia.org/wiki/FICON
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: A Complete History Of Mainframe Computing Newsgroups: alt.folklore.computers Date: Fri, 10 Jul 2009 14:42:46 -0400"Charlie Gibbs" <cgibbs@kltpzyxm.invalid> writes:
as undergraduate in the late 60s, i did a lot of stuff with (virtual
machine) cp67 timesharing system ... some past posts
https://www.garlic.com/~lynn/submain.html#timeshare
including added ascii/tty terminal support. the native cp67 terminal support had "automatic" terminal type identification differentiating between 1052 & 2741 terminals. Adding ascii/tty terminal support, i exented the automatic recognition to include ascii/tty (w/o reguiring predefined configuration).
The 2702 terminal controller had "SAD" command that allowed associating specific terminal-type linescanner with any port address ... which facilitated the automatic terminal identification/operation on any port. This worked fine for "leased" lines where the connected terminal didn't actually change. I wanted also to have a single/common dialup number for all terminal types ... that served "rotory" pool of ports. This didn't quite work since the 2702 took an implementation shortcut ... "SAD" command allowed dynamically changing association of terminal-type specific linescanner with any port ... but the shortcut was they hardwired linespeed oscillator to each port (i could change any port between 1052, 2741, & tty/ascii linescanner ... but couldn't couldn't dynamically change linespeed baud rate).
This somewhat prompted univ. to start a clone controller effort; reverse
engineer mainframe channel interface, build clone channel interface
board for Interdata/3 ... and program the Interdata/3 to emulate 2702
terminal controller. The software interface in Interdata/3 to port
allowed sampling signal raise/lower ... as way of dynamically
determining line speed (overcomming the 2702 hardwired limitation).
some past posts
https://www.garlic.com/~lynn/submain.html#360pcm
Now a primary motivation for future system project
https://www.garlic.com/~lynn/submain.html#futuresys
was to provide such high integration between processor and controllers that it significantly raised the bar for clone controllers ... reference:
https://www.ecole.org/en/session/49-the-rise-and-fall-of-ibm
quote from above:
IBM tried to react by launching a major project called the 'Future
System' (FS) in the early 1970's. The idea was to get so far ahead that
the competition would never be able to keep up, and to have such a high
level of integration that it would be impossible for competitors to
follow a compatible niche strategy. However, the project failed because
the objectives were too ambitious for the available technology. Many of
the ideas that were developed were nevertheless adapted for later
generations. Once IBM had acknowledged this failure, it launched its
'box strategy', which called for competitiveness with all the different
types of compatible sub-systems. But this proved to be difficult because
of IBM's cost structure and its R&D spending, and the strategy only
resulted in a partial narrowing of the price gap between IBM and its
rivals.
... snip ...
while future system effort failed ... there is observation that the SNA tight integration between pu5/vtam & pu4/ncp reflected the future system project (in fact, there were jokes that SNA architecture wasn't a documented specification ... but whatever pu5/vtam happened to support). However, it wasn't really a network implementation but targeted at support humongous number (tens or hundreds of thousands) of terminals (or other kinds of devices likes tens or hundreds of thousands of ATM cash machines).
Nearly 20 yrs after the 2702 clone controller project ... I got involved
with one of the baby bells that had done a 37xx clone using S/1s ... but
providing significantly more function ... some past posts:
https://www.garlic.com/~lynn/99.html#66
https://www.garlic.com/~lynn/99.html#67
https://www.garlic.com/~lynn/99.html#69
https://www.garlic.com/~lynn/99.html#70
one of the other limitation was mainframe had half-duplex channel/io
architecture ... recent reference
https://www.garlic.com/~lynn/2009j.html#59
In the HSDT (high-speed data transport) project ... misc. posts
https://www.garlic.com/~lynn/subnetwork.html#hsdt
there were some use of NSC HYPERchannel adapters ... and A220/A222 adapter boxes that attached to mainframe channels. The A22x adapter boxes provided pool of 64 (sub)channel addresses. Most of the implementations tended to assign subchannel address to specific function but use it them traditional half-duplex manner. One of my big issues was increasing latency issues ... so I did a design that was "dual" simplex and dynamically assigned subchannel addresses for outgoing and incoming operation (as work-around to half-duplex operation).
the internal network (backbone) did something analogous for 56kbit (full-duplex) telco links. They built a Y-adapter that took full-duplex telco link and split it into incoming and outgoing signals and plugged it into pairs of controller ports ... and then software programming simulated full-duplex with pairs of ports, one dedicated for incoming and one dedicate for outgoing.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: A Complete History Of Mainframe Computing Newsgroups: alt.folklore.computers Date: Sat, 11 Jul 2009 10:44:24 -0400Anne & Lynn Wheeler <lynn@garlic.com> writes:
one of the issues with incoming (7bit) ascii ... was that the 8th bit could be parity ... so translate tables were specified as "even parity", "odd parity" or "no parity".
one of the early issues with the interdata/3 as 2702 clone was how 2702 linescanners worked (sort of momentary glitch that was overlooked). first attempt at terminal data from the interdata/3 appeared to be all garbage. after some investigations and reflection ... the interdata/3 was taking bits off the port and treating as byte for transfer to mainframe memory.
2702 linescanners took leading bit and placed it in low-order (byte) bit position ... so incoming bytes were "bit reversed" ... comparerd to what bit sequence would appear on the line ... so the mainframe ascii translate tables were "bit reversed" bytes (in addition to issue of even/odd/no parity). As a result, 2702 clone/interdata3 had quick patch to do similar bit reversal.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: An Information Gap Sparks a Dust-Up over Remote Key Injection Date: 9 July, 2009 Blog: Financial Crime Risk, Fraud and SecurityAn Information Gap Sparks a Dust-Up over Remote Key Injection
from above:
However, our customers and vendors can use remote key injection
services to upgrade the terminals if those services meet all aspects
of the PCI PIN security requirements.
... snip ...
earlier article:
MasterCard halts remote POS security upgrades
http://www.networkworld.com/news/2009/072409-paypal-opens-door-to.html
from above:
In a purported second major security change in recent weeks,
MasterCard has decided to disallow merchants' use of remote key
injection (RKI) services to install new encryption keys on
point-of-sale (POS) systems, says a Gartner analyst
... snip ...
MasterCard seeks to clarify remote POS security upgrades policy
http://www.computerworld.com/s/article/9135428/MasterCard_seeks_to_clarify_remote_POS_security_upgrades_policy
from above
Today's statement referred to the need for RKI "services" to be
compliant with PCI standards, while making no mention of the need for
the devices to be compliant. MasterCard did not respond to a request
for further clarification.
... snip ...
The computerworld article makes it sound more like financial incentive for processors to get PCI certified. Other articles have talked about the significant financial costs to processors (and merchants) for PCI certification.
One of the other RKI articles mentioned that merchants were looking to save money on (electronic/remote) key loading (even for devices that weren't PCI certified), since processors were only going to charge half as much for electronic/remote key loading compared to having person come out and do manual key load. Presumably the cost to the processor for electronic/remote key loading is only small percentage of cost of having human visit to do manual key load ... which then might make it quite a profit center.
Tying that processor profit to PCI certification ... might be construed as inducement for certification.
slightly related thread regarding end-to-end encryption and provisioning costs:
https://www.garlic.com/~lynn/2009j.html#26 Price Tag for End-to-End Encryption: $4.8 Billion, Mercator Says
https://www.garlic.com/~lynn/2009j.html#29 Price Tag for End-to-End Encryption: $4.8 Billion, Mercator Says
https://www.garlic.com/~lynn/2009j.html#58 Price Tag for End-to-End Encryption: $4.8 Billion, Mercator Says
Price Tag for End-to-End Encryption: $4.8 Billion, Mercator Says
http://www.digitaltransactions.net/newsstory.cfm?newsid=2250
from above:
Meanwhile, the final tab for the solution is no small matter. A
point-of-sale terminal with end-to-end encryption starts at $500 for a
mom-and-pop merchant and goes up for multi-lane retailers, the report
notes.
... snip ...
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: A Complete History Of Mainframe Computing Newsgroups: alt.folklore.computers Date: Sat, 11 Jul 2009 19:05:03 -0400Quadibloc <jsavard@ecn.ab.ca> writes:
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: A Complete History Of Mainframe Computing Newsgroups: alt.folklore.computers Date: Sun, 12 Jul 2009 09:32:03 -0400Quadibloc <jsavard@ecn.ab.ca> writes:
we got the story about 3270 terminals being "expensive" ... but we did the calculations that monthly amortized 3yr depreciation (assuming customer price, not internal transfer price) was about the same per month as standard business phone (business phone cost was driving factor for businesses to go to in-house PBX in the 80s). it was accepted that business phone was standard on desks ... so why weren't 3270 terminals (since they weren't any more expensive). turned out that lots of 3270s had lifetime closer to ten yrs (so actually much less, especially if internal price was considered).
but then i've pontificated that driving factor for big uptake of business IBM/PCs in the 80s was that they were about the same price as 3270 (which lots of businesses already justified) ... about the same desk footprint ... and in single footprint could do duty as both 3270 emulations and local personal computing (there was almost no incremental business case to justify changing budget allocated for 3270s to buying IBM/PCs instead). big corporations looking at having tens of thousands of 3270s for employees ... was relatively minor effort to switch to IBM/PCs.
before the mac was announced ... i got to have the argument with some of the apple people ... since they weren't planning on having business use &/or terminal emulation for the mac.
but then later ... communication division was big barrier moving on to things like client/server ... since they were focused on protecting their large terminal emulation customer install base.
lots of past posts mentioning terminal emulation
https://www.garlic.com/~lynn/subnetwork.html#emulation
in the later 80s, we had come up with 3-tier architecture and were out
pitching to customer executives ... and taking lots of barbs from the
communication forces (in the midst of trying to protect terminal
emulation install base with things like SAA) ... misc. posts
https://www.garlic.com/~lynn/subnetwork.html#3tier
The communication division was out pitching token-ring LANs for IBM/PCs and 3270 terminal emulations ... so that was a little hardware transition. 3270 terminal emulation market was experiencing some problems ... a real problem for some businesses was that bldg. 3270 coax cables were starting to exceed some bldg. weight bearing limits ... every 3270 terminal had its own coax cable running all the way back to the datacenter. In addition the incremental cost of laying one additional 3270 coax cable could be as much as ibm/pc price.
Token-ring configurations could have single wire to local departmental utility closet ... and then individual terminals wired to the utility closet. Eventually token-ring (cat-5) wiring was done in new bldgs as standard along with phone wiring.
AWD (workstation division) had done its own 4mbit T/R (16bit ISA) card for the PC/RT ... but then was forced to use the PC's division 16mbit T/R (32bit microchannel) card for the RS6000. The PC's division 16mbit T/R card had the terminal emulation design point ... huge number (300+) of "terminals" all sharing same 16mbit bandwidth. As a result, "thruput" for a 16mbit T/R microchannel card was actually lower than what the PC/RT 4mbit T/R ISA card could do. A PC/RT "server" with a 4mbit T/R card could sustain higher thruput than RS6000 "server" with a 16mbit T/R card (i.e. bandwidth requirements in client/server environment is asymmetrical ... server needing to sustain the aggregate bandwidth of all the individual clients)
I mentioned using NSC HYPERchannel for channel extended ... provide
"local" 3270 service for 300 people from IMS group that had been
relocated to offsite bldg ... but getting their dataprocessing back in
the STL (now silicon valley lab) datacenter ... recent post
https://www.garlic.com/~lynn/2009j.html#40 My "Green Screen" IBMLink is still working
some mention using NSC HYPPERChannel also in this post (for
higher speed networking)
https://www.garlic.com/~lynn/2009j.html#60 A Complete History Of Mainframe Computing
To try and get around the bottleneck problem for RS6000 servers (imposed
by being forced to use the PC groups "terminal emulation" 16mbit T/R
adapter) ... we talked NSC into adding an "SLA" interface to NSC
high-speed routers. The biggest problem was the enormous amount of
internal paperwork and approvals required to allow "selling" SLA
interface chips to NSC (another corporate road block they tried to throw
up was 1000%-2000% markup on the chips ... we tried to argue that NSC
was doing us a favor and we should be providing them free). It would
then be possible to configure RS6000 servers with SLA interface to NSC
high-speed routers ... and their high-speed routers had their own LAN
interfaces (high-performance ethernet & T/R to client environment ... as
well as T1 & T3 telco interfaces). Recent mention of SLA (along with
FCS, escon, and ficon):
https://www.garlic.com/~lynn/2009j.html#59 A Complete History Of Mainframe Computing
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Infosec As a Form of Asymmetric Warfare Date: 11 July, 2009 Blog: Information Security NetworkInfosec As a Form of Asymmetric Warfare
from above:
There are an amazing number of parallels between The Art of War and
the information security business. In its very basic form - knowing
your enemy - knowing how cyber vandals, miscreants, crime
... snip ...
I'm a little biased ... having sponsored John Boyd's briefings at IBM in the 80s (some have described him as greatest strategic thinker since Sun Tzu).
random reference:
https://www.amazon.com/review/R2YT33FKBMVMAJ
from above:
... and how his ideas have spawned the 4th Generation and Asymmetric
Warfare theories, for which the Pentagon does not yet have an adequate
appreciation
... snip ...
a few other references:
Cyberwar And The OODA-Loop
http://gramatoncleric.gnn.tv/blogs/23059/9_11_Cyberwar_And_The_OODA_Loop
Gathering dimensions of conflict into a unified model
http://selil.com/?p=531
The New Face of War: How War Will Be Fought in the 21st Century
http://www.foreignaffairs.com/articles/58827/lawrence-d-freedman/the-new-face-of-war-how-war-will-be-fought-in-the-21st-century
OODA-Loop
https://en.wikipedia.org/wiki/OODA_Loop
misc. past posts mentioning Boyd:
https://www.garlic.com/~lynn/subboyd.html#boyd1
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: A Complete History Of Mainframe Computing Newsgroups: alt.folklore.computers Date: Sun, 12 Jul 2009 14:02:04 -0400TrailingEdgeTechnologies <bbreynolds@aol.com> writes:
recent post also mentioning in '79 getting 3101 ("topaz", glass teletype)
at home to replace cdi miniterm
https://www.garlic.com/~lynn/2009j.html#40 My "Green Screen" IBMLink is still working
old post with (very poor quality) picture of my home 3101:
https://www.garlic.com/~lynn/2008m.html#51 Baudot code direct to computers?
original was 3277 with 3272 controller ... which was followed by 3278 with 3274 controller. we had even done some "human factors" enhancements to 3277. we complained that when 3278 came out ... it wasn't even as good as 3277 ... and since they moved a lot of electronics out of terminal back into the controller (significant reduced manufacturing costs), we couldn't make any engineering corrections. I kept 3277 around at work into mid-80s.
Old post mentioning 3277/3278 when 3278 first came out:
https://www.garlic.com/~lynn/2001m.html#19 3270 protocol
we were told that issues we were raising about 3278 were with regard to "interactive computing" ... and 3278 wasn't targeted for "interactive computing" ... but for "data entry" market.
misc. other past posts mentioning 3101 (/topaz ... original code name)
https://www.garlic.com/~lynn/99.html#69 System/1 ?
https://www.garlic.com/~lynn/2000g.html#17 IBM's mess (was: Re: What the hell is an MSX?)
https://www.garlic.com/~lynn/2001b.html#12 Now early Arpanet security
https://www.garlic.com/~lynn/2001b.html#13 Now early Arpanet security
https://www.garlic.com/~lynn/2001h.html#32 Wanted: pictures of green-screen text
https://www.garlic.com/~lynn/2001m.html#1 ASR33/35 Controls
https://www.garlic.com/~lynn/2001m.html#54 Author seeks help - net in 1981
https://www.garlic.com/~lynn/2003c.html#34 difference between itanium and alpha
https://www.garlic.com/~lynn/2003c.html#35 difference between itanium and alpha
https://www.garlic.com/~lynn/2003n.html#7 3270 terminal keyboard??
https://www.garlic.com/~lynn/2004e.html#8 were dumb terminals actually so dumb???
https://www.garlic.com/~lynn/2005p.html#28 Canon Cat for Sale
https://www.garlic.com/~lynn/2005r.html#12 Intel strikes back with a parallel x86 design
https://www.garlic.com/~lynn/2006n.html#56 AT&T Labs vs. Google Labs - R&D History
https://www.garlic.com/~lynn/2006y.html#0 Why so little parallelism?
https://www.garlic.com/~lynn/2006y.html#4 Why so little parallelism?
https://www.garlic.com/~lynn/2006y.html#24 "The Elements of Programming Style"
https://www.garlic.com/~lynn/2006y.html#31 "The Elements of Programming Style"
https://www.garlic.com/~lynn/2007e.html#15 The Genealogy of the IBM PC
https://www.garlic.com/~lynn/2007h.html#39 sizeof() was: The Perfect Computer - 36 bits?
https://www.garlic.com/~lynn/2007k.html#40 DEC and news groups
https://www.garlic.com/~lynn/2007t.html#74 What do YOU call the # sign?
https://www.garlic.com/~lynn/2008l.html#79 Book: "Everyone Else Must Fail" --Larry Ellison and Oracle ???
https://www.garlic.com/~lynn/2008m.html#37 Baudot code direct to computers?
https://www.garlic.com/~lynn/2008m.html#38 Baudot code direct to computers?
https://www.garlic.com/~lynn/2008m.html#51 Baudot code direct to computers?
https://www.garlic.com/~lynn/2008m.html#88 Sustainable Web
https://www.garlic.com/~lynn/2008n.html#51 Baudot code direct to computers?
https://www.garlic.com/~lynn/2008r.html#5 What if the computers went back to the '70s too?
https://www.garlic.com/~lynn/2008s.html#22 IBM PC competitors
https://www.garlic.com/~lynn/2009c.html#30 I need magic incantation for a power conditioner
https://www.garlic.com/~lynn/2009d.html#13 Typewrite repair?
https://www.garlic.com/~lynn/2009g.html#45 Netbooks: A terminal by any other name
https://www.garlic.com/~lynn/2009h.html#32 My Vintage Dream PC
https://www.garlic.com/~lynn/2009j.html#40 My "Green Screen" IBMLink is still working
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: DCSS Date: Mon, 13 Jul 2009 07:20:37 -0400 Newsgroups: bit.listserv.vmesa-lChip Davis wrote:
To provide read-only protection of those three pages, CP67 played special games with the 360 storage protect keys.
Moving to 370, original 370 virtual memory architecture (defined in the 370 "red book" ... the "red book" was cms script file with command line options would print the full architecture book ... or just the principles of operation subset) had 64kbyte segment options and 1mbyte segment options. For 370, CMS was restructured to have the 1st 64k non-shared & data, and the 2nd 64k "shared" ... using the 370 64kbyte shared segment facility. The original 370 virtual memory architecture also had R/O segment protect facility ... bit defined in each virtual memory segment table which would provide R/O segment protection. vm370 was initially implemented to use this facility for protecting shared pages. The mechanism was still the defined named systems and invoked/used via the ipl-by-name facility.
the retrofit of virtual memory hardware to 370/165 ran into delays and at one point there was suggestion to drop a lot of the 370 virtual memory features in order to buy back six months in the scheduled (and not slip the 370 virtual memory announcement by six months). One of the features that got dropped was "segment protect". As a result, all the other hardware implementations had to go back and remove all the features dropped by the 165 implementation ... and vm370 had to return to the (kludge) r/o page protection mechanism using the 360 key protect mechanism (from cp67) ... but for whole segments.
I was at the science center ... past posts mentioning science center
https://www.garlic.com/~lynn/subtopic.html#545tech
csc/vm (&/or sjr/vm) posts
https://www.garlic.com/~lynn/submisc.html#cscvm
and we were still running with 360/67 and doing lots of enhancements
to cp67. One of the features was a page-mapped filesystem faciilty for
cms. This eliminated a whole lot of I/O simulation overhead and
pathlength (even compared to diagnose I/O ... a form of which I had
originally done as undergraduate) and opened up the ability to do a
whole lot more interesting things using virtual memory (basically
allowing page mapped views of anything done as part of standard cms
"file" operations ... not just restricted to ipl-by-name). Misc. past
posts mentioning page-mapped work for cms filesystem
https://www.garlic.com/~lynn/submain.html#mmap
Eventually, science center was slated for getting at 370/155 and I had
to look at moving lots of my cp67 work to vm370 ... old memo on the
subject
https://www.garlic.com/~lynn/2006v.html#email731212
and a couple describing having done the work (and what was in the
"csc/vm" distribution system)
https://www.garlic.com/~lynn/2006w.html#email750102
https://www.garlic.com/~lynn/2006w.html#email750430
one of my hobbies had been providing highly modified cp67 systems to internal locations (sort of my own product distribution). that dropped off as some number of internal locations moved from cp67 to vm370 ... but really took off when I had moved from cp67 to vm370.
One of my major hobby/customers was the HONE system ... lots of past
posts
https://www.garlic.com/~lynn/subtopic.html#hone
HONE had been created after the 23jun69 unbundling announcement ... originally cp67 virtual machine systems originally targeted at giving branch office SEs "hands-on" to operating systems running in virtual machines. The HONE system even got special CP67 modifications that simulated the initial new instructions in 370 ... allowing running/testing of 370 operating systems that used the new instructions (i.e. allowing them to run in virtual machine under cp67 on 360/67.
The science center had also ported apl\360 to cp67 cms for cms\apl. A lot of sales & marketing support applications were developed in APL and started to be offered to sales & marketing. Eventually that use came to dominate HONE activity and the virtual machine experience for branch office SEs evaporated.
APL had been restructured to "shared memory" operations and originally HONE had a special "ipl-by-name" APL ... which put sales&marketing into APL only environment. However, there was some requirement to have non-APL applications to be run ... and it was extremely awkward to have sales & marketing people issue the IPL command to switch between APL and non-APL applications.
So one of the first big uses of page-mapped filesystem and new shared segment mechanism was HONE APL use with early flavor of CSC/VM). Whether or not a page-mapped file was loaded as non-shared or shared ... were new parameters that could be specified when the module was "generated" (genmod) ... and supported by kernel program loading facility.
Many of the internal 370 organizations slacked off on product
development during the height of future system activity (since future
system was going to replace all 360 & 370 ... and was significantly
different that 360/370)
https://www.garlic.com/~lynn/submain.html#futuresys
when future system was killed ... there was mad rush to get things back into the 370 hardware and software pipelines ... including vm370. Since I had continued to do 370 stuff all during the future system days (even making various criticism of future system stuff) ... I had a lot of unreleased 370 stuff.
In any case, some amount of stuff from CSC/VM distribution was picked up for inclusion in VM370 Release 3. Part of that was CMS changes for additional shared segments (including work to make things "shareable" that hadn't previously been R/O protect) ... but not the page mapped filesystem. As a result, the additional CMS shared-segment stuff had to be mapped into the ipl-by-name facility and allowed to be invoked w/o going through the rest of the IPL simulation.
This is what was called DCSS in VM370 Release 3.
The posts containing the above email has some additional discussions
about a very small subset of the paged-mapped filesystem support being
released as DCSS
https://www.garlic.com/~lynn/2006w.html#7
https://www.garlic.com/~lynn/2006w.html#8
https://www.garlic.com/~lynn/2006w.html#9
Also picked up from CSC/VM for VM370 Release 3 was the "autolog" command, which I had originally done for automated benchmarking.
---
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: DCSS addenda Date: Mon, 13 Jul 2009 08:04:42 -0400 Newsgroups: bit.listserv.vmesa-lre:
Some of the other stuff in CSC/VM was released in my resource manager (which appeared with vm370 release 3 plc9)
the 23jun69 unbundling announcement started charging for (application)
software and se services (but they managed to make the case that
kernel software should still be free). some posts mentioning
unbundling
https://www.garlic.com/~lynn/submain.html#unbundle
When I was undergraduate ... I had added tty/ascii terminal support to
cp67 ... and tried to make the 2702 do something it couldn't quite
do. that somewhat was motivation behind the univ. starting a project
for a clone controller using interdata/3 ... discussed some in this
recent post
https://www.garlic.com/~lynn/2009j.html#60 A Complete History Of Mainframe Computing
four of us got written up being responsible for clone controller
business. some posts mentioning clone controller
https://www.garlic.com/~lynn/submain.html#360pcm
The clone controller business has been attributed as the motivation for the FS project.
https://www.ecole.org/en/session/49-the-rise-and-fall-of-ibm
quote from above:
IBM tried to react by launching a major project called the 'Future
System' (FS) in the early 1970's. The idea was to get so far ahead that
the competition would never be able to keep up, and to have such a high
level of integration that it would be impossible for competitors to
follow a compatible niche strategy. However, the project failed because
the objectives were too ambitious for the available technology. Many of
the ideas that were developed were nevertheless adapted for later
generations. Once IBM had acknowledged this failure, it launched its
'box strategy', which called for competitiveness with all the different
types of compatible sub-systems. But this proved to be difficult because
of IBM's cost structure and its R&D spending, and the strategy only
resulted in a partial narrowing of the price gap between IBM and its
rivals.
... snip ...
old post with somebody taking FS quotes from Fergus&Morris book on IBM
https://www.garlic.com/~lynn/2001f.html#33 IBM's "VM for the PC" c.1984??
Now allowing 370 product pipelines dry up is claimed to have given the clone processors foothold in the market ... and success of the clone processors is major motivation to decide to start (also) charging for kernel software. My resource manager got chosen to be the guinea pig for kernel software charging ... and as a result ... I had to spend some amount of time with the business people & lawyers on policies regarding software charging.
another mad rush to get products back into the 370 product pipeline
was the 303x stuff ... recent discussion
https://www.garlic.com/~lynn/2009j.html#59 A Complete History Of Mainframe Computing
basically after FS was killed, work on 3081 was started but that was going to take 6-7 yrs ... and they needed something on much shorter cycle ... so 3031 was repackaged 370/158, 3032 was repackaged 370/168, and 3033 started out as 168 wiring diagram remapped to newer chips that were 20% faster.
Now one of the things that were in the page-mapped filesystem stuff was location independence support. Carefully crafted executable code could be loaded at any virtual location in any virtual address space. The same "shared" object could appear at different virtual addresses in different virtual address spaces. Operating systems that had been designed for paged-mapped operations had support for this as a matter of course ... including IBM's TSS/360.
CMS inherited a lot of its structure, compilers and other features from os/360 ... which had a real-storage orientation. OS/360 Relocatable address constants ... were relocated at "load" time ... and while executing were tied to a specific address. This nominally prevented having the same shared object appearing simultaneously in multiple virtual address spaces at different addresses.
The 370 issue was that with only 256 64kbyte segments (in 16mbyte
virtual address space) ... there would be great difficulty in finding
unique locations for every application that might be available at a
large location. Any single user wouldn't necessarily require more
than 16mbytes ... but might require an arbitrary combination of
applications available at the installation. To support shared "fixed"
address applications which might be used in arbitrary combination... a
unique location had to be chosen for ever application ... but the
total possible aggregate size of all available applications exceeded
16mbytes. Lots of past posts mentioning difficulty of modifying code
so it would be location independent while executing (in addition to
having to modify it for executing in a R/O protected shared segment)
https://www.garlic.com/~lynn/submain.html#adcon
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: 64 Cores -- IBM is showing a prototype already Newsgroups: alt.folklore.computers Date: Mon, 13 Jul 2009 09:02:46 -0400Morten Reistad <first@last.name> writes:
unregulated, non-depository loan originating institutions could use securitization as source of funds. being able to "buy" triple-A ratings for their asset-backed securities, allowed them to sell-off every loan they could write w/o regard to borrowers qualification or quality of loan.
with the repeal of Glass-Steagall, a large amount of these securities found their way to regulated depository institutions with their unregulated investment banking arms buying them up and carrying them off-balance (basically regulated depository institutions, in a circuitous manner bypassing regulations, were providing lots of the funding for this activity).
Bank's Hidden Junk Menaces $1 Trillion Purge
>http://www.bloomberg.com/apps/news?pid=newsarchive&sid=akv_p6LBNIdw&refer=home
from above:
So investors betting for quick solutions to the financial crisis could
be disappointed. The tangled web that banks wove over the years will
take a long time to undo.
At the end of 2008, for example, off-balance-sheet assets at just the
four biggest U.S. banks -- Bank of America Corp., Citigroup Inc.,
JPMorgan Chase Co. and Wells Fargo Co. -- were about $5.2 trillion,
according to their 2008 annual filings.
... snip ...
there are numerous articles about slight-of-hand accounting rules to keep these toxic (asset-backed) securities off-balance to avoid forcing the institutions into bankruptcy.
a few past posts mentioning above:
https://www.garlic.com/~lynn/2009h.html#79 The $4 trillion housing headache
https://www.garlic.com/~lynn/2009i.html#60 In the USA "financial regulator seeks power to curb excess speculation."
https://www.garlic.com/~lynn/2009i.html#77 Financial Regulatory Reform - elimination of loophole allowing special purpose institutions outside Bank Holding Company (BHC) oversigh
https://www.garlic.com/~lynn/2009j.html#35 what is mortgage-backed securities?
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: 64 Cores -- IBM is showing a prototype already Newsgroups: alt.folklore.computers Date: Mon, 13 Jul 2009 12:12:20 -0400sidd <sidd@situ.com> writes:
long-winded, recent pontification
https://www.garlic.com/~lynn/2009j.html#35 what is mortgage-backed securities
one of the recent references:
Lobbyists on a Roll: Gutting Reform on Banking, Energy, and Health
Care
http://www.huffingtonpost.com/arianna-huffington/lobbyists-on-a-roll-gutti_b_220521.html
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: 64 Cores -- IBM is showing a prototype already Newsgroups: alt.folklore.computers Date: Mon, 13 Jul 2009 14:30:06 -0400sidd <sidd@situ.com> writes:
there was news show yesterday with geithner interview ... i didn't catch the first of the show ... so don't know whether it was live or not.
interviewer started with why didn't gov. take AIG into bankruptcy so that less than 100 cents on the dollar would be paid out on valid contracts to Goldman and the other big new york financial institutions ... which is common practice in similar situations.
geithner interrupted in the middle to say that some large european financial institutions also got AIG money.
geithner then answered the question by saying that these were valid contracts with AIG and that is why 100 cents on the dollar were paid out.
since the question was about taking AIG into bankruptcy so that it wouldn't be necessary to pay 100 cents on the dollar ... it would appear that the subtext of the answer is that the they wanted to pay out 100 cents on the dollar.
today one of the tv business news show hosts ... who normally comes out quite strong against gov. regulations on things like caping executive compensation and other issues ... repeatedly made a big deal about possibility that the strong financial showing of large new york financial institutions were because of the AIG payouts ... and at some point there will have to be a settling at Goldman and the other institutions.
recent AIG article:
Michael Lewis on A.I.G. vanityfair.com
http://www.vanityfair.com/politics/features/2009/08/aig200908?printable=true¤tPage=all
then there is the Rolling Stone's Goldman article ... referenced here:
Who caused the financial crisis - villains or jerks? - Money Features
http://moneyfeatures.blogs.money.cnn.com/2009/07/11/who-caused-the-financial-crisis-villains-or-jerks/
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: A Complete History Of Mainframe Computing Newsgroups: alt.folklore.computers Date: Mon, 13 Jul 2009 15:02:12 -0400Peter Grange <peter@plgrange.demon.co.uk> writes:
weekly lawn watering and a class break coincided ... with corresponding large number of flushes ... resulted in big drop in water pressure (affecting cooling).
a few past posts mentioning berkeley's 6600:
https://www.garlic.com/~lynn/2002d.html#6 IBM Mainframe at home
https://www.garlic.com/~lynn/2008i.html#57 Microsoft versus Digital Equipment Corporation
https://www.garlic.com/~lynn/2008i.html#96 A Blast from the Past
https://www.garlic.com/~lynn/2009c.html#14 Assembler Question
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: DCSS ... when shared segments were implemented in VM Date: 13 July, 2009 Blog: Mainframe Experts Networkseveral recent posts in the (ibm mainframe) virtual machine mailing list over the past day or two about when was DCSS support added to VM. Original VM370 "shared segments" were only via the ipl-by-name faciilty part of emulating the IPL command.
a couple of my long winded posts regarding the subject
https://www.garlic.com/~lynn/2009j.html#67
https://www.garlic.com/~lynn/2009j.html#68
for something different, long ago and far away ... I got told that even if I provided fully tested and integrated FBA support for MVS ... it would still cost $26M for documentation and education ... and that there needed to be business case that covered that $26M ... aka new/additional sales on the order of $200M. Supposedly at the time, the claim was that customers would buy the same amount of FBA instead of CKD (so there wouldn't actually be any new/additional sales). The argument that there would be long-term life cycle cost savings wasn't allowed as justification to cover the $26M.
some past posts mentioning getting to play disk engineer in
bldg. 14&15 (disk engineering and disk product test labs)
https://www.garlic.com/~lynn/subtopic.html#disk
some past posts mentioning CKD &/or FBA issues
https://www.garlic.com/~lynn/submain.html#dasd
and as in previous reference ... posts mentioning having done (CMS)
page-mapped filesystem (originally for cp67)
https://www.garlic.com/~lynn/submain.html#mmap
the page mapped filesystem obtain some additional performance thruput ... some of it by eliminating the channel I/O emulation (even compared to cms diagnose i/o ... a form of which I had originally done for cp67 as undergraduate in the 60s).
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Apollo 11: The computers that put man on the moon Newsgroups: alt.folklore.computers Date: Mon, 13 Jul 2009 18:59:01 -0400Apollo 11: The computers that put man on the moon
from above:
By today's standards, the IT Nasa used in the Apollo manned lunar
programme is pretty basic. But while they were no more powerful than a
pocket calculator, these ingenious computer systems were able to guide
astronauts across 356,000 km of space from the Earth to the Moon and
return them safely.
... snip ...
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: 64 Cores -- IBM is showing a prototype already Newsgroups: alt.folklore.computers Date: Tue, 14 Jul 2009 09:19:33 -0400Anne & Lynn Wheeler <lynn@garlic.com> writes:
business tv news shows are continuing to repeat the above question several times this morning ... along with quotes along the lines of "gov. has been bought and paid for by the financial industry".
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: CMS IPL (& other misc) Date: Wed, 15 Jul 2009 07:00:18 -0400 Newsgroups: bit.listserv.vmesa-lAdam wrote:
CMS started out with 256kbyte (virtual) machine operation (on real 360/40).
original virtual machine system (at science center) was cp/40 done on a (256kbyte) 360/40 that had special hardware modification to support virtual memory.
while cp/40 was being developed ... cms was also being developed ... running on the "bare" 360/40 in non-virtual memory mode.
when the science center replaced the 360/40 with 360/67 (standard product, basically 360/65 with hardware modifications to support virtual memory) ... cp40 morphed into cp67
when 3 people from the science center came out to install cp67 at the univ the last week of jan68 ... all source was kept on cards on loaded into os/360 and assembled under os/360 producing physical text decks ... which were combined together in a card tray with a modified BPS "loader" in the front. The physical cp67 deck was loaded into 2540 card reader and ipl. after BPS "loader" got the CP67 "txT" decks into memory ... it would transfer to the last program ... CPINIT (in vm370 DMKCPI) ... which would write the core image to specified disk location and write the IPL CCW sequence to the IPL disk.
Distribution was os/360 tapes.
CMS would run in a 256kbyte virtual machine or on the "bare" hardware.
Part of the issue was both CP40 (and then CP67) and CMS were being developed in parallel ... with the original source compile, etc ... all being done on os/360.
Sometime by summer 68, science center had moved to having source as CMS files and assembling on CMS to produce "TXT" decks. Physical "TXT" were still being kept in card tray and physically IPL to build new IPL'able kernel.
By that summer, I had done a lot of kernel CP67 pathlength work
... especially targeted for OS/360 in CP67 virtual machine. Old post
with part of presentation I gave at the fall68 SHARE meeting (held in
atlantic city) ... lots of changes were picked up by the science center for
standard cp67 and shipped
https://www.garlic.com/~lynn/94.html#18 CP/67 & OS MFT14
I was also doing very carefully crafted OS/360 stage2 sysgens. I originally would get the stage2 card deck output from the OS/360 stage1 assemble ... and reorder all the statements to achieve carefully order of resulting generated system file on disk (to optimize arm seek operation).
Later in 68, I looked at doing some pathlength enhancements for CMS environment (as well as starting on dynamic adaptive resource management, new page replacement algorithms, new scheduling algorithms and other stuff). Lots of CMS operation was simplified (compared to OS/360) ... so major (cp67) pathlength overhead was in CMS disk I/O channel program translation (CCW). I originally defined a "new" CCW op-code that in single CCW specified all the parameters for seek/search/tic/read/write operation ... drastically reducing the channel program translation overhead. I also noticed that CMS didn't do any multitasking ... just did serialized wait for the disk i/o to complete. So I gave this new CCW op-code serialized semantics (i.e. it actually returned to virtual SIO after the I/O had completed, with CC=1 CSW stored).
I got a lot of push back from the science center about having "violated" virtual machine architecture (a CCW that wasn't defined in any hardware manual). They explained that the appropriate way to violate the 360 principles of operation was with the "diagnose" instruction ... which was defined as being "model" dependent implementation. The fiction was then to define a virtual machine "hardware model" ... where the operation of the diagnose instruction were according to virtual machine (model) specification.
CMS was modified to use "a" diagnose instruction at startup to determine whether it was running in virtual machine or (instruction "failed") on real machine. If running in virtual machine, it would be setup to use diagnose instruction for diak i/o (semantics about the same as my special CCW) or SIO (& interrupts) for disk I/O.
In the initial translation to VM370 (release 1), CMS (cambridge monitor system) was renamed to CMS (conversational monitor system) and the test for running in virtual machine was removed as well as the code to use SIO (& interrupts) for disk I/O ... eliminating CMS's ability to run on bare hardware.
In cp67 there was a facility for saving "named" virtual memory pages and ipl-by-name virtual memory pages. The NAME specifications were part of a kernel module (renamed DMKSNT for VM370). In cp67, the named tables specified the range of virtual pages to be saved (and the disk location where they were to be saved). The "ipl-by-name" would modify virtual memory tables to point to the specified disk location (with RECOMP bit ... that the disk location was R/O to the page replacement algorithm ... the page could be fetch from that location ... but when it was to be replaced, it had to go to a newly, recomputed disk location).
360/67 only had 1mbyte virtual segment sizes ... which weren't useful for virtual memories that typically smaller than 1mbyte ... so cp67 implemented "shared pages". The named specification could optional specified certain pages that were to be "shared" (as part of the ipl-by-name). The first time ipl-by-name was invoked for a named system, the "shared pages" were brought into real storage and "fixed". For then on ... all other ipl-by-names (for that system) would have their virtual memory page table entries set to those (fixed) real pages. For CMS, this originally was 3 pages. Protection as achieved by fiddling with the os360 storage protect keys (and not allowing cms to be dispatched with a psw in "real" key zero).
As previously mentioned, CMS & saved/shared names systems was reorganized for vm370 to take advantage of 370 64kbyte segments (16 4k virtual pages) ... and originally the 370 segment protect facility. Unfortunately because of 370/165 hardware schedules, 370 segment protection was one of the things dropped out of the announcement ... and vm370 had to retrofit the cp67 key fiddling, storage protect mechanism.
I did page mapped filesystem for cp67 ... eliminating the need to have "named systems" ... and in morph to vm370 had a large set of feature/functions I referred to as "virtual memory management" ... arbitrary virtual memory pages could be mapped to filesystem page locations along with support for arbitrary shared segment operation. As mentioned, most of the these changes for CMS "shared operation" were picked up (new portions of CMS code redone to run in R/O shared/protected segments, CMS editor redone to run in R/O shared/protected segment, etc) were picked up for vm370 release 3. However since all the page mapped filesystem support was being picked up ... the stuff was remapped to DMKSNT "saving" & "loading" using DCSS diagnose.
The full page mapped filesystem had a bunch of additional capability ... in addition to significantly reducing virtual machine simulation overhead (for file system operations) ... even compared to the CMS diagnose I/O implementation. It could also provide for asynchronous execution overlapped with I/O ... w/o having asynchronous support in CMS (by fiddling page invalid bits) ... this was done dynamically based on load and configuration and operations being performed.
In the early 80s, I did a project that took the kernel spool file system and moved it into a virtual address space ... with the implementation being redone is vs/pascal. The objective was to make it run at least ten times faster for all sorts of operation ... and the capability and thruput leveraged the paged mapped filesystem support.
One of the issues was that I had started the HSDT project (high-speed
data transport) ... some number of past posts
https://www.garlic.com/~lynn/subnetwork.html#hsdt
with lots of T1 (full-duplex 1.5mbit, about 300mbyte/sec aggregate) and faster links. nominal vnet/rscs was using spool file interface ... which was synchronous 4k byte operations ... maybe 30-40 ops/sec if there was no spool file contention ... possibly 4-5 ops/sec on heavily loaded system (20kbytes/sec). For RSCS/VNET with 9.6kbit links it wasn't bad ... but I could easily need 3-4mbyte/sec thruput (instead of 20kbyte-30kbyte/sec).
For other topic drift ... also started working with NSF on T1 links
for something that was going to become the NSFNET backbone (the
operation precursor to the modern internet). Somewhere along the way,
there was some internal politics and were prevented from bidding on
NSFNET backbone. The head of NSF tried to help by writing the company a letter 3Apr1986, NSF Director to IBM Chief Scientist and IBM Senior VP and director of Research, copying IBM CEO) ... but that seemed to just
aggravate the internal politics (statements like what we already had
running was at least five yrs ahead of all bid submissions for
building something new). misc. old email
https://www.garlic.com/~lynn/lhwemail.html#nsfnet
misc. past posts
https://www.garlic.com/~lynn/subnetwork.html#nsfnet
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: More named/shared systems Date: Wed, 15 Jul 2009 11:57:17 -0400 Newsgroups: bit.listserv.vmesa-lJeff wrote:
and post in similar thread that I started in linkedin mainframe discussion
https://www.garlic.com/~lynn/2009j.html#73
I mentioned that Cambridge had done port of apl\360 to (cp67) cms for
cms\apl. This then became one of the main vehicles for deliverying
sales & marketing support on (virtual machine based) HONE (first cp67
and then moved to vm370 ... eventually with HONE clones all over the
world) ... some past HONE clones
https://www.garlic.com/~lynn/subtopic.html#hone
a quick "named version" was done by getting APL started and then getting it at a certain point and doing a named system ... that was not only CMS but also APL. Then when IPL'ed ... the machine was placed immediately at a point in APL (special place chosen so it would do some last minute housekeeping and setup). One of the univ. did something similar for ipl-by-named version of os/360.
for vm370 ... palo alto science center did a lot of additional stuff for apl\cms (including the apl microcode assist on the 370/145).
For early "vanilla" vm370, HONE started out with ipl-by-name apl\cms ... with the addition that the cms shared segment was defined as well as most of the APL executable module and even some APL "workspace". A early problem had some non-APL applications and had issue with trying to explain to salesman (which were mostly hardly computer literate users) how to IPL CMS ... to execute non-APL applications and then IPL APL ... to get back into the normal (APL-based) sales & marketing environment.
When I started distributing "CSC/VM" with the enhancements, HONE was one of the major internal clients (they even con'ed me into doing several of the early "clone" installations around the world). With the paged-mapped filesystem and the enhanced changes ... most sales&marketing could (automatically at login) IPL normal CMS and have their profile setup to immediately execute APL (cms executable from "S" or "Y" disk that happened to be paged mapped format) ... and all the page mapping and shared segment was done as part of normal CMS program loading.
Then it was possible to have APL processes that would invoke and execute non-APL applications ... even placing the user in the non-APL application environment w/o having to explain to the user about the IPL command or some of the other non-APL (there was a large sales&marketing APL application called SEQUOIA that actually hid nearly all APL & CMS characteristics from the sales & marketing people ... it was even possible that many sales & marketing people never realized that they were using APL &/or CMS).
I've several times told the story that between middle 70s until at least middle 80s .. every couple yrs there would be a promotion of some sales/marketing person to the head of the dataprocessing business unit that included HONE. They would be startled to find that HONE was VM370/CMS based and figure that they could make their career by forcing HONE to be ported to MVS. This would consume the HONE organization for possibly 12 months until it was extremely evident that it wasn't practical. Then things would almost return to normal (for a few months) until the next person was promoted into the position.
As I've mentioned ... a small subset of the (shared/named) capabilities was shipped in vm370 release 3 as DCSS. It was then possible for ("normal") customers to define APL as a named system w/o requiring the paged mapped filesystem support.
One of the early issues with port of APL\360 for CMS\APL ... there was a big performance issue with how APL did storage allocation and (periodic) garbage collection. The problem wasn't noticed in a "real workspace" environment of APL\360 where the whole workspace was swapped as single unit. CMS/APL opened workspace up to nearly the full virtual machine size (which might be 16mbytes) ... and the garbage collection performed terribly in virtual memory paged environment (LISP had something similar) ... and had to be significantly redone.
the port to CMS\APL also added APL functions that could access CMS system services ... including ability to read & write files (which the APL purists criticized as corrupting the APL purity). However, the significant increase in workspace size (from typical os/360 of 16kbytes or 32kbytes) and being able to do things like file I/O ... allowed some "real" applications to be implemented. For a while, a big user of CMS\APL on the cambridge cp67 system was corporate business planning people in armonk which loaded the most sensitive of all corporate data ... actual customer data ... and they were doing business modeling.
This created something of security issue for the cambridge system ... having the highest classified and most sensitive corporate data ... as well as a lot of non-employee users ... mostly from educational institutions in the boston/cambridge area (students and professors).
for the fun of it ... a semi-related reference to cp67 being used in
environments with high security needs:
https://web.archive.org/web/20090117083033/http://www.nsa.gov/research/selinux/list-archive/0409/8362.shtml
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Gone but not forgotten: 10 operating systems the world left behind Newsgroups: alt.folklore.computers Date: Wed, 15 Jul 2009 12:10:14 -0400Gone but not forgotten: 10 operating systems the world left behind; AmigaOS, CP/M, OS/2, DOS -- which OS do you miss the most?
for a little topic drift ... some recent archived posts to the mainframe
vm mailing list regarding cp67/cms from the 60s (and vm370 from the 70s)
https://www.garlic.com/~lynn/2009j.html#67 DCSS
https://www.garlic.com/~lynn/2009j.html#67 DCSS addenda
https://www.garlic.com/~lynn/2009j.html#73 DCSS ... when shared segments were implemented in VM
https://www.garlic.com/~lynn/2009j.html#76 CMS IPL (& other misc)
https://www.garlic.com/~lynn/2009j.html#77 More named/shared system
and then there are past references to the CP/M named being derived from
Gary Kildall having used CP/67 at NPG in monterey
https://www.garlic.com/~lynn/2001b.html#52 Kildall "flying" (was Re: First OS?)
https://www.garlic.com/~lynn/2004h.html#40 Which Monitor Would You Pick??????
https://www.garlic.com/~lynn/2006.html#48 Early microcomputer (esp i8008) software
https://www.garlic.com/~lynn/2007d.html#41 Is computer history taugh now?
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Timeline: The evolution of online communities Newsgroups: alt.folklore.computers Date: Wed, 15 Jul 2009 12:48:36 -0400Timeline: The evolution of online communities
from above:
E-mail discussion lists, chat rooms, BBSs, Usenet groups and more all
played a role in the development of online communities as we know them
today.
... snip ...
cp67 & vm370 had real time messages on the same real system and then
supported by rscs/vnet that would forward such messages between remote
systems ... internal network was larger than arpanet/internet from just
about the beginning until sometime late '85 or early '86.
https://www.garlic.com/~lynn/subnetwork.html#internalnet
Tymshare supported online conferencing early 70s ... and made the
facility "free" to SHARE VM group in Aug76:
http://vm.marist.edu/~vmshare/
in the late 70s and early 80s I got blamed for online computer
conferencing on the internal network doing semi-automated mailing
list operation ... recent reference in this n.g.
https://www.garlic.com/~lynn/2009e.html#26 Microminiaturized Modules
the above some major motivation behind "official" effort that resulted in the internal TOOLSRUN ... which could simultaneously operate somewhat similar to USENET and mailing list (i.e. somebody could subscribe as mailing list ... or setup TOOLSRUN "client" that would subscribe and maintain local repository of posts).
Listserv on BITNET, misc. past posts
https://www.garlic.com/~lynn/subnetwork.html#bitnet
was somewhat to duplicate at least part of the TOOLSRUN function
discussed here (starting Paris, 1985 ... i.e. the EARN part of BITNET)
http://www.lsoft.com/products/listserv-history.asp
related email (from Paris) regarding setting up EARN
https://www.garlic.com/~lynn/2001h.html#email840320
in this post
https://www.garlic.com/~lynn/2001h.html#65
and looking for network-oriented applications for the educational institution users.
There is also example of the distributed evolution of the REX language
implementation in the late 70s and early 80s (leveraging the internal
network) ... some discussion here:
http://www-01.ibm.com/software/awdtools/rexx/library/rexxhist.html
and here:
https://web.archive.org/web/20020506063424/http://computinghistorymuseum.org/ieee/af_forum/read.cfm?forum=10&id=21&thread=7
the author of rexx ... had also done a multi-user space war game for cms (on 3270s) that used the rscs/vnet forwarding interface to extend the game into distributed environment across multiple machines in the network.
somewhat as the result for getting blamed for online computer
conferencing on the internal network in the late 70s and early 80s
... there was a researcher that was paid to sit in the back of my
office for nine months and take notes on how I communicated (as well
go with me to meetings). They also got copies of all my incoming and
outgoing email as well as logs of all my instant messages. The result
was an internal corporate report ... but also Stanford Phd thesis
(joint between language and computer AI) as well as some number of
papers and books ... misc. past posts mentioning computer mediated
conversation
https://www.garlic.com/~lynn/subnetwork.html#cmc
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Timeline: The evolution of online communities Newsgroups: alt.folklore.computers Date: Wed, 15 Jul 2009 15:38:36 -0400re:
and somewhat related ... hot off the presses
RFC 5598, Internet Mail Architecture, D. Crocker
Abstract
Over its thirty-five-year history, Internet Mail has changed
significantly in scale and complexity, as it has become a global
infrastructure service. These changes have been evolutionary, rather
than revolutionary, reflecting a strong desire to preserve both its
installed base and its usefulness. To collaborate productively on this
large and complex system, all participants need to work from a common
view of it and use a common language to describe its components and the
interactions among them. But the many differences in perspective
currently make it difficult to know exactly what another participant
means. To serve as the necessary common frame of reference, this
document describes the enhanced Internet Mail architecture, reflecting
the current service. This memo provides information for the Internet
community.
... snip ...
my RFC index
https://www.garlic.com/~lynn/rfcietff.htm
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: 64 Cores -- IBM is showing a prototype already Newsgroups: alt.folklore.computers Date: Thu, 16 Jul 2009 10:19:25 -0400re:
supposedly AIG rogue operation starting writing CDS as unlicensed insurance policies for (toxic, asset-backed) CDO losses. then they got into writing CDS as form of (unlicensed) gambling on whether there would be losses on (toxic, asset-backed) CDOs (the distinction about this being rogue operation was that there were no provisions for reserves to ever having to pay off on the CDS ... either for the insurance form to those actually taking losses on CDOs or to those that were purely making bets on whether or not CDOs would have losses; CDS (insurance/betting) "premiums" were being treated as 100% profit for purposes of determining bonuses).
Part of the ambiquity around the (taxpayer funded) AIG CDS payoffs is avoiding making distinction between the unlicensed insurance form and the unlicensed betting form ... i.e. organization not actually having any CDS and/or taking any losses ... sort of like taking out "insurance policy" on somebody else's automobile and getting a payout if that person ever has an accident ... AND the taxpayer providing the funds for the betting payoff). In the case of Goldman ... on one side they have AIG making huge CDS (betting) payouts to Goldman at the same time there is all the press that Goldman was smart enough to not have any significant deals/losses in toxic asset-backed CDOs.
item from January:
Bailed-Out Banks Dole Out Bonuses; Goldman Sachs, CitiGroup, Others
Mum on How They Are Using TARP Cash
http://abcnews.go.com/WN/Business/story?id=6498680&page=1
from above:
Goldman Sachs, which accepted $10 billion in government money, and lost $2.1 billion last quarter, announced Tuesday that it handed out $10.93 billion in benefits, bonuses, and compensation for the year.
... snip ...
referenced in this post
https://www.garlic.com/~lynn/2009.html#73 CROOKS and NANNIES: what would Boyd do?
more recent:
'Even A Chimpanzee Could Run Goldman Sachs'
http://news.hereisthecity.com/news/business_news/9227.cntns
some of the news items are that given the enormous (taxpayer funded) betting payoff, that easily dominated all other activity.
other posts mentioining abc news item:
https://www.garlic.com/~lynn/2009.html#80 Are reckless risks a natural fallout of "excessive" executive compensation ?
https://www.garlic.com/~lynn/2009b.html#25 The recently revealed excesses of John Thain, the former CEO of Merrill Lynch, while the firm was receiving $25 Billion in TARP funds makes me sick
https://www.garlic.com/~lynn/2009b.html#41 The subject is authoritarian tendencies in corporate management, and how they are related to political culture
https://www.garlic.com/~lynn/2009b.html#49 US disaster, debts and bad financial management
https://www.garlic.com/~lynn/2009b.html#57 Credit & Risk Management ... go Simple ?
https://www.garlic.com/~lynn/2009b.html#59 As bonuses...why breed greed, when others are in dire need?
https://www.garlic.com/~lynn/2009e.html#17 Why is everyone talking about AIG bonuses of millions and keeping their mouth shut on billions sent to foreign banks?
https://www.garlic.com/~lynn/2009j.html#36 Average Comp This Year At Top Firm Estimated At $700,000
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970